[Famous Teacher Crossing] Recommended thesis of the Editorial Committee of "Network Security Governance"
Author:Information security research Time:2022.08.13

"Cyber Security Governance" is the eighth special direction of "Information Security Research" in 2022. The teacher of the responsible editorial committee of this issue is Dr. Yan Bing, director of the National Internet Emergency Center Runction Department, recommends this special paper for everyone. Welcome everyone to read a message.
▶ Special recommendation thesis
"APT Attack Detection Research under LSTM -based Linux system" (Author: Shilin, Shi Shaosen, Wen Weiping, unit: Peking University Software and Microelectronics Academy)
"Malid Blockchain Domain Testing Methods based on convolutional neural networks" (Author: Wang Zhonghua, Xu Jie, Han Jian, Zang Tianning, unit: National Computer Network Emergency Technology Treatment Coordination Center, China Industrial Internet Research Institute, China Academy of Sciences Information Engineering Project graduate School)
"APT attack detection research under LSTM -based Linux system"
▶ Thesis recommendation reason
Senior continuous threat (APT) attack has been the focus and hot issue in the field of network security in recent years. APT attacks often have strong organizational backgrounds such as the country. The attack is high, the stealing secrets, and the concentrated eruption at a certain time is extremely harmful to national security. Most of the APT attacks use encrypted communication. As traffic encryption becomes more and more common, the APT attack traffic is hidden in ordinary encryption flows, and it is difficult to find. Discovering APT attacks in time has important theoretical significance and practical value for maintaining national security and reducing people's losses.
Combining the application needs of APT attack detection, the paper proposes the APT attack dataset construction method, the APT attack detection method based on machine learning theory, and explores the key difficulties in the field of network security monitoring. The thesis system is complete, the discussion is rigorous, and the research selection has practical significance. It has strong practical value and guiding significance for how to carry out the research work of APT attack detection.
▶ Responsible editorial board comment
The thesis built a set of APT attack datasets with the characteristics of the host behavior and network behavior, which better solves the problem of the current lack of high -quality APT attack dataset in the industry; combined with machine learning methods, propose a LISTM -based Linux system The next APT attack detection scheme has achieved a good attack detection effect by introducing the timing of the APT attack into the detection detection. The paper has strong reference significance for the research on the APT attack detection, and has high reference value for engineering practice.
▶ The main content
The thesis is mainly divided into 4 parts: based on the comprehensive introduction of the characteristics of the APT attack, the research status of the APT attack detection technology is analyzed; the construction method of the APT attack data set is explained; Methods; detailed the experimental situation, and analyzed the impact of different parameters on the analysis results.
"Method of malicious blockchain domain name detection method based on convolutional neural networks"
▶ Thesis recommendation reason
With the development of blockchain technology, the combination of blockchain technology and domain name analysis technology, blockchain domain names, namely BDNS. Malicious blockchain domain names quickly become an important means for hackers to control zombie networks. Compared with the traditional domain name system, the blockchain domain name has the same things and many new characteristics. Traditional malicious domain name detection methods are not all suitable for malicious blockchain domain name detection. The detection of malicious blockchain domain names is a new problem and new challenge facing the field of network security. Studying malicious blockchain domain names have strong practical value.
By conducting a detailed analysis of the characteristics of malicious blockchain domain names, the paper proposes a convolutional neural network algorithm suitable for malicious blockchain domain name detection, and achieves efficient discovery of malicious blockchain domain names. The paper discusses comprehensive and strong systematic, providing a valuable reference for academic research and the development of related technological development in the industry.
▶ Responsible editorial board comment
The thesis explores the difference between the blockchain domain name and the traditional domain name, in -depth analysis of the resource records and traffic behavior of the malicious blockchain domain name, propose the characteristics of extracting domain names from multiple dimensions, processed by one, and use convolutional neural networks. Training classification models to detect malicious blockchain domain names, and achieve efficient testing of malicious blockchain domain names. The thesis divides the characteristics of malicious blockchain domain names into two aspects: static characteristics and behavioral characteristics. The thesis method can effectively tap the association between the different characteristics of a single domain name. The probability of detecting the failure of the domain name due to the falsification of a single characteristics was reduced, and the detection effect was improved. The paper has high academic significance and practical value.
▶ The main content
The thesis is mainly divided into three parts: the application background, malicious domain name detection technology, and the development of the blockchain domain name system development of blockchain evil domain name detection technology are introduced; Methods gave detailed algorithm structure; analyzed and discussed the experiments.
[Editorial Committee of responsibility in this issue · Personal profile]
The severe ice, doctorate, professor -level senior engineer. Graduated from the Computer Department of Tsinghua University. He is currently the director of the operating department of the National Internet Emergency Center. He has been engaged in the handling of national Internet security emergency incidents, the operation of the national Internet security monitoring platform, and the research of new technology tracking of network security. Hosted key projects of many national natural science funds, national natural science funds projects, and national science and technology support plans. Get a number of provincial and ministerial rewards.
- END -
Data Basic System Construction of Foundation Digital Age
The new round of scientific and technological revolution and industrial changes ar...
Refresh the world record!
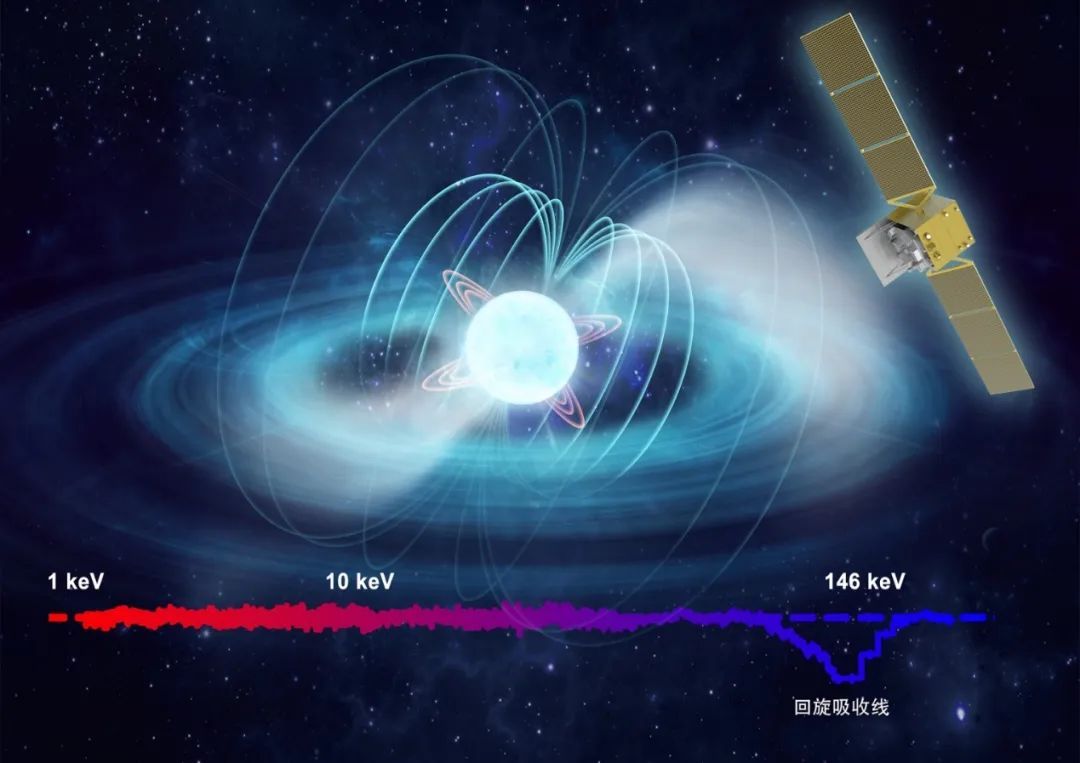
Recently, the my country Eye Satellite Team found that the neutron X -ray two star...