Dry goods | Tsinghua University Ye Xiaojun's "Information Security Technology Big Data Service Security Requirements" national standard revision thinking
Author:Data School Thu Time:2022.08.29
The content of this article is organized from the "Information Security Technology Big Data Service Security Requirements" by the "Information Security Technology Big Data Service Security Requirements" national standard revision thinking.

Let me introduce to you some of our feelings of GB/T 35274-2017 "Information Security Technology Big Data Service Security Requirements" led by Tsinghua University. Today, the report includes the following parts: 1) Background of Standard Amendment 2) Standard Amendment 3) Introduction to Standard Content 4) Standard Revision and thinking 5) Subsequent work arrangements.
First review the background of the revision of the standard. In 2016, the National Information Technology Security Standardization Committee (referred to as the Xin'an S standard Commission) established a special working group of big data security standards, emphasizing that industrial development needs standards first. Another important but not disclosed is that in 2016, the State competent department organized a big data security self -assessment for network security censorship. Because of such industrialized demand and national security protection goals, the National Internet Information Office (referred to as the Internet Information Office) hopes that the big data security special working group will formulate relevant standards. After review by the Standard Application Application Application and the Special Working Group of the Big Data Security Specialty Working Group, the 2016 Big Data Security Special Working Group has three standards to get the project. The first is the code of personal information security protection, the second is the requirements of big data service security capabilities, and the third is big data security management guidelines. The amendment of the national standard system has a certain period. Generally speaking, the standards of five years need to be evaluated on the standards of standards. Therefore, in early 2021, we launched the application for the establishment of this standard revision, and in August 2021, it was notified by the establishment of the CITS Standard Standard Standard Standard.
Today's theme of the conference is very good, because data security and data elements are specially concerned by the country and industry. The situation at the time of the GB/T 35274 standard was not so good, because the terms and definitions related to related big data, data security, data processing and other related terms were still irregular. At that time, many regulatory documents formulated by this standard were not available. Therefore, the standard formulation faces many challenges. For example, there were basically no reference standards to formulate materials at the time, and the organization lacked regulations to guide the standards of standards. Therefore, the establishment principles adopted by the establishment group can only be autonomous preparation. Fortunately, many domestic Internet platform companies such as Alibaba, Huawei, Tencent, etc. in China have done a good job in big data services. Their best practice provides standard preparation provides standard preparation. Material. Second, the national authoritative evaluation agencies have also accumulated some related data on big data security assessment. For example, the cloud security review organized by the Internet Information Office has done a good job. "Requirements can guide the preparation of this standard, including the ISO/IEC 27001 information security management system widely recognized by domestic enterprises, and the US NIST SP1500 big data security interoperability series standards can be referred to. In the end, it is necessary to point out that the "Big Data Security White Paper", which is co -prepared by the Big Data Security Special Working Group, has also promoted the preparation of this standard.
After the GB/T 35274 was approved in July 20011, after nearly a year of hard work, the review was formed in June 2017, and it was officially promulgated in December 2017. In the process of standard preparation, we invited all domestic Internet platform companies that engaged in big data business in order to summarize their best practices into this standard. On the one hand The summary, on the other hand, is also the practicality of the standard content from the perspective of network security review, to guide related tasks such as big data security assessment and data outbound evaluation of the Internet Information Office, including data from the national level on the domestic Internet platform. Resources have comprehensive assessment of its security control measures, and at the same time guide other big data service providers to build their big data system in accordance with this data service capabilities.
The above is the background and goals of the GB/T 35274 standard. The amendment background is mainly the coordination of regulations compliance and standards. For example, the "Cyber Security Review Measures" has not been promulgated when we formulate GB/T 35274. During the implementation of the GB/T 35274, you can see that the Internet Information Office is constantly in the iterative review method, and three versions have been launched. There are also several regulations such as the "Data Security Law" and "Personal Information Protection Law", which are specially related to our standards, and several regulations such as the "Regulations on the Management of Network Data Security (Draft for Opinions)" in the past two years have also been promulgated. The GB/T 35274-2017 formula we used to cross the river from the bottom of the river we used to touch the river needs to be replaced by the downward and downward and in accordance with the requirements of the regulatory requirements. Another revision background is to ensure the coordination and consistency. Because during the formulation of this standard in 2016, the revision of the underlying technology and platform related network security level protection series of big data services has not been completed. In the past five years, the amendments to the requirements of cloud computing service security capabilities have been basically completed, and the relevant supporting standards of the "Information Security Technology Personal Information Security Protection Specifications" have been formulated, including the Credit and Settlement Committee in the past two years around the "Data Security Law" of the Data Security Law And the "Personal Information Protection Law", such as the "Information Security Technology Network Data Classification Holmonning Requirements". Special reminder, the state may make it a mandatory national standard for the "Internet Data Classification and Holding Requirements". Therefore, the state competent department recommends that the letter of the "network" of the "network" is also modified to the "information security technology data classification classification classification classification grading ", This shows that the country attaches great importance to the work of data classification. Under such a background, the establishment team has determined the amendment goal of this standard. Unlike the previous 2017 version positioning, the 2017 version is a standard for formulating the work for network security review. The supporting standards of the development of the data industry GB/T 37988 "Best Security Technology Data Security Capability Mature Model". This ability model is organized, and the GB/T 35274 capabilities requirements are graded from the four aspects of organizational construction, institutional process, technical tools and personnel capabilities.

The national standard emphasizes the coordination of standards, combined with the requirements of data security management systems and data security risk management in the laws and regulations of the digital security law, and the management of data security risks. We have made great adjustments to the standard structure. In addition The organizational management security capabilities and data processing activity security capabilities in the original standard have added special emphasis on the requirements of data service risk security management capabilities in the revision of the standard. Therefore, this amendment mainly stipulates the requirements of its big data service security capacity building requirements from the perspective of big data service providers.
These two PPT briefly introduced the basic process of revising this standard. The current standard revision work is in the standard application pilot work stage.
As a national security standard, we must first meet the relevant demands of the competent authorities in accordance with the standard positioning, and at the same time, it must be recognized by relevant enterprises and users. After the successful revision of the standard revision in July 2021, the preparation group revised the working procedure in accordance with the standard system of the big data security special working group, introduced the draft draft, working group draft, and solicitation drafts of the Standard Meeting Week, and invited relevant experts many times to invite relevant experts Review. During the application verification process of the standard pilot application, the Cyber Security Bureau of the Ministry of Industry and Information Technology attaches great importance to this standard, especially the data service risk management section, and supplement many compliance feedback suggestions on the standard structure and standard terms in accordance with relevant regulations.

Regarding the standard content, the core of personal understanding is the term selection and definition, and the relationship between the standard and other standards. When this standard was formulated in 2016, the Data Security Law has not been proposed, and the relationship between data security and network security is not clear. In the "Data Security Law" in 2021, it has been clearly stated that data security should be protected on data security in the network security protection system, and activities related to data security definition and data processing are given. Therefore, in the standardized documents, this revision special emphasis should be added to the basic requirements for the protection of network level protection, and the requirements of the information security management system related to the organization of data security management should be added. In addition, the current data concepts in the digital economy and big data environment, including data processing concepts, are different from data and data processing in traditional databases. Therefore, we also supplemented the "Information Technology Terms" standard in standardized documents. Increase these three standardized standards, so that the standards are better coordinated with other standards.
Chapter III's terms and definitions are standard universal structures. This revision we have made a big adjustment of this part. Because we think that terms and definitions are necessary to explain the standard topics. For example, the data life cycle is particularly emphasized when formulating this standard in 2016, but the newly issued "Data Security Law" does not mention the data life cycle. This is because the data life cycle is generally aimed at a certain object, an organization or a system system. Essence So we deleted the term of the data life cycle. In addition, the original standard data services, data exchange, and data sharing are inappropriate. Therefore, these terms are deleted. In addition, after years of development, the industry has a new understanding of big data platforms, big data applications, big data systems, and big data services, so we have also improved these terms with the times. In particular, there are several core activities definitions in the data processing in the Data Security Law and Personal Information Protection Law. Therefore, in this standard, we clearly supplement data collection, data use, data, data Definition of processing and other terms. For terms that are inappropriate for the definition of the term, does the big data system contain the data assets it manages and control? After many discussions, the compilation team believes that big data service providers should have big data systems, and big data systems should include data resources required by their services. Therefore, in the definition of big data systems, the data provided by the data supply chain is implicitly provided by the data supply chain. concept. This PPT is about the newly added term definition sample. We clearly define the use of data use and data processing. The following note explains the external causes of the two terms, which clarifies the difference in data use and data processing. Several core concepts of new data processing activities, we haven't seen in the current relevant national standards, but in the "Data Security Law" and "Personal Information Protection Law" are very important concepts, so we think it is necessary to define Essence What we are gratified is that our big data platform and data supply chain are newly revised in the GB/T 35274-2017 standard. Because these terms have been cited in large quantities in the relevant standards of the Big Data Security Special Working Group. We also hope that the added term will be recognized in future related standards.
Below we introduce the revision of the standard content structure. The fourth chapter before the revision includes three subtitles: overall requirements, standard grading and standard structure. Essence This time we removed the first two sections and improved the standard structure content of the third part.
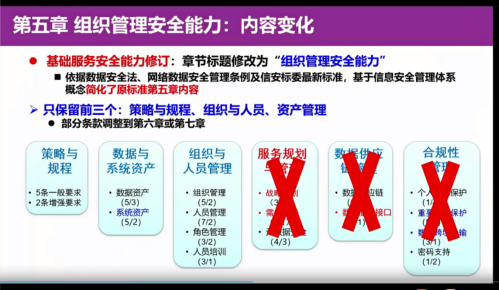
According to the 5th chapter of the standard, we only retain the core content of organizational management. The title 5 of the original standard is the basic service capacity requirements. This revision only retains the strategy and regulations and regulations, organizational and personnel management and data and system asset management of organizational management. The three parts of sexual management are adjusted to the subsequent chapters, and only the core content related to the organization of information security management is retained.

Chapter 5 In addition to the adjustment of the standard structure, the standard terms inside have also been modified. For example, the strategy and regulations in the original standards include five general requirements and two enhancement requirements. The revised strategies and regulations include ten clause requirements, and each clause contains multiple sub -clauses. In general, the strategy and regulations are mainly related to the requirements of the "Data Security Law" to improve the requirements of the entire process data security management system around the "Data Security Law". As far as this revision is concerned, the preparation group focuses on national laws and regulations and management regulations on data security related to the data security incidents in recent years. legality.
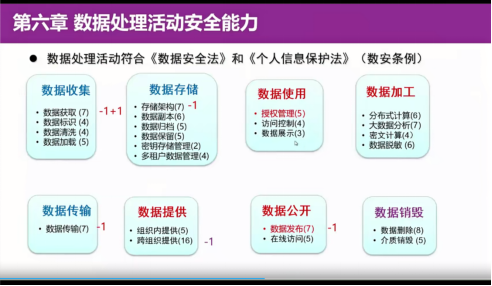
Chapter 6 The content of the data processing activity is the security ability. The title of Chapter 6 of 2016 is data service security capabilities. It needs to be added that the title of the 6th chapter 6 in June 2016 is the security ability of the data life cycle, but during the development process, it is considered that different organizations and different serve them The data life cycle is different, so the data life cycle should not be used in standards. When discussing the security capabilities of the data service mainly include the activities, the relevant standard specifications are differently defined for the data life cycle. The compilation team shall be determined that this standard shall include data collection, transmission, storage, processing, exchange, and destroy the destroyer of the six stages of the six stages. Essence These six stages were also adopted by many relevant standards of the Xin'an Tiber Committee. Even so, our revision this time in accordance with the relevant regulations such as the data security law, we modified the original data processing to the eight data processing activities required by the number of laws, and reorganized the content of the data service terms in the original standard.
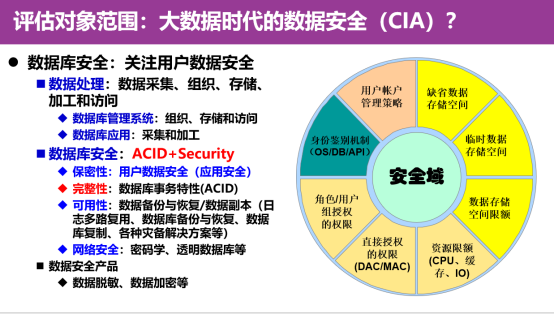
Chapter 7 is about data service risk management security capabilities, mainly to solve the level of cross -data activity (that is, data activity portfolio), and facing the management security requirements for organizational business and data security operation -related service risks. Data operation combinations of various data activities during big data services cause security risks such as data operation or data operation. In this chapter, according to the requirements of the data business circulation process and data processing activities in the big data service, the security capabilities of the establishment of data service risk management from the six links of risk recognition, security protection, security monitoring, security inspection, security response, and security restoration. Take risk response measures to ensure that data services and data assets in big data system operations are always in a secure protection state in order to control the data security risks of cross -data activity or data flowing in different IT spaces. Finally, we want to discuss our thinking in the revision of this standard. The first is the scope of the standard assessment object clear. This standard is an organization that requires data resources required for big data platforms, big data applications and big data services. The big data platform is different from the database management system. Traditional database security mainly refers to protecting the confidentiality of user data. Data integrity and availability are based on database transaction characteristics and database management system transaction logs, data backup, log archives and other data redundancy or systems. The redundancy is realized, but the security function requirements of the big data platform are still changing. This is because the underlying storage model of the big data platform is still being optimized. The relevant transaction characteristics have not been supported by most platforms, including big data service capabilities, etc. No consensus is formed. Therefore, the security technical capacity requirements of the big data platform need to be defined clearly in order to write clearly in the standard terms. At present, these technical contents are not reflected in the terms of the sixth and seventh chapters.

What is the connotation of big data in the second big aspect? In the past, we said that big data is defined from 4V features. This 4V feature is actually described from the perspective of information technology, but it is not enough to define the concept of big data security. Safety issues in space. Finally, the data has a life cycle. It is necessary to consider the security requirements of various laws and regulations in different activities in different activities. Therefore, when we discuss the requirements of big data services security capabilities, we need to comprehensively describe the relevant information security, functional security caused by data -driven services, and personal information protection in big data systems. Capability requirements.
In short, for the formulation of a standard specification, we must first make a clear concept of evaluation objects and related terms, and the relevant standards and their relationship positioning can be effectively organized to effectively organize standard content. The standard is the summary of the best practice. Therefore, it is necessary to communicate extensively and invite relevant experts for review. At present, this standard has entered the stage of improvement of the submission review. The later preparation team will improve the standard terms based on the feedback of this pilot work. The establishment team also hopes to do some of the data security law and personal information protection law of my country through this modification. Work that can do. Just as we formulated and implemented the improvement of the organization's data security management capabilities through GB/T 37988-2019 in the early stage. In the future, we also want to promote the management of the organization's data factor in the revision of the GB/T 37988 standard to ensure the legitimacy of the organization's data security management And compliance. Data factor governance and data security standardization work has been on the road. We will continue to work hard to jointly develop the development of my country's big data industry in the industry and promote the advancement of big data security technology. The above is my personal report, thank you all.




- END -
"Isn't it that the sciences!" After returning to work, they entered the "Accelerated Run" mode

Text | China Science News reporter Zhang NanThe Tianma telescope, which had been st...
3 Kaili!Guizhou 2022 The fourth batch of the list of small and medium -sized enterprises intended to be entered into the warehouse

A few days ago, the Guizhou Provincial Department of Science and Technology announ...