How did the boss find that you touch fish at work?
Author:Institute of Physics of the Ch Time:2022.06.19
The resumption of work means that the days of home office (touching fish) are about to end.

And Shanghai's "Mei Mei" made the commuting commute very difficult.

The dense umbrella of the subway station inlet
Picture source: Shanghai Metro Shmetro
Nothing and place, one has not taken up, it is too difficult to last class, but the more "difficult" may still be behind.
Touching the fish at work and being "grab"
Around the Spring Festival this year, two reports from the company's discovery of the company were discovered on the Internet because of touching fish.

One is the internal notification of a home appliance group, which detailed the traffic situation of employees' interviews with non -working content during working hours, and the other report was that one employee submitted resumes in the working hours and was discovered by the company installed. Essence
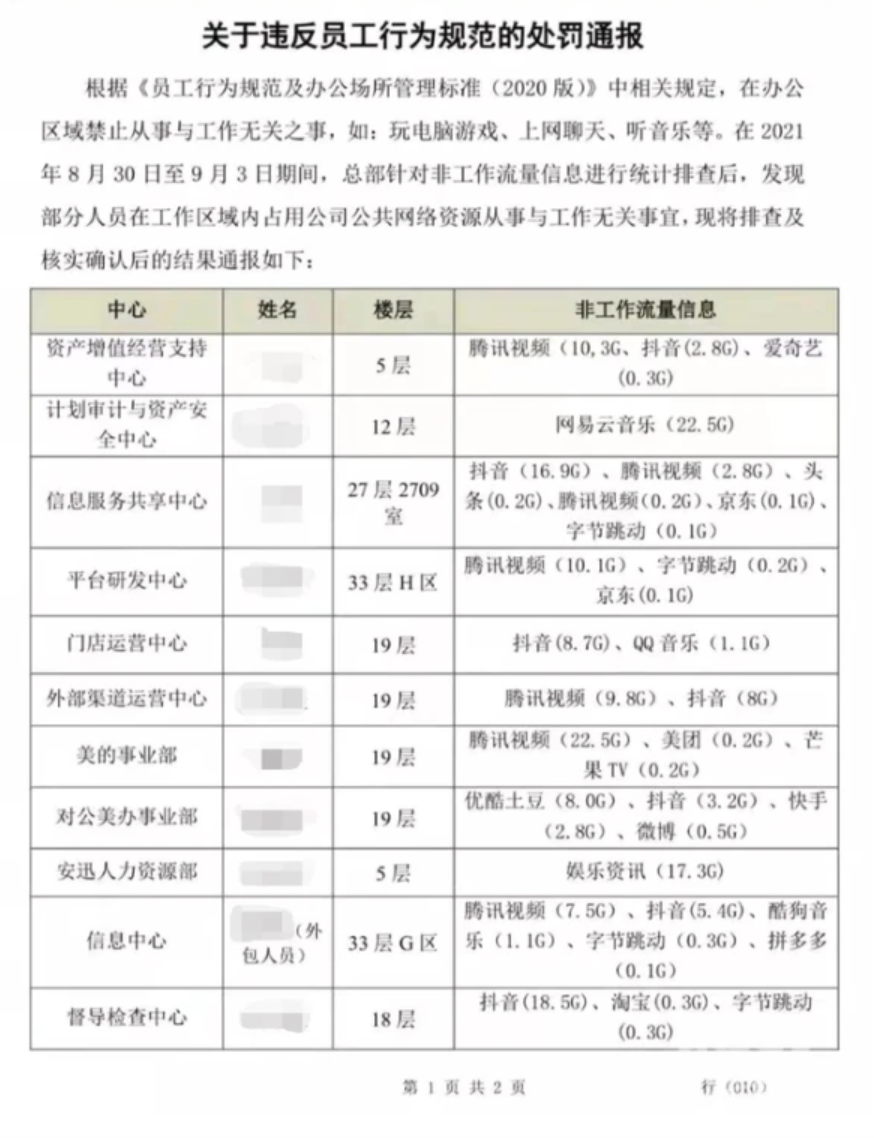
Notification part of the content
Picture source: Metropolis Express
Network transmission monitoring system picture
Picture source: Guangzhou Daily
For a while, the discussion about touching fish and anti -touched fish was very arrogant, and at the same time, a question led to a problem. How did the bosses find that the employees were touching the fish when they were at work?
Two mainstream
Enterprise network management plan
At present, there are two mainstream corporate network management solutions, one is to install behavior management software, and the other is to analyze traffic characteristics.

Before 2015, the more popular online behavior management software. In contrast, its gold content is low, and the specific operation method is to install relevant monitoring software on the company's office computers in order to record the fishing behavior.
The general principle is to collect the use of employee computers by regular screenshots, process monitoring, traffic records, and file changes.

But with the improvement of everyone's computer technology and operating system security, this kind of software similar to Trojan is easily unloaded by employees. At the same time, the behavior of screenshots is also very easy to cause legal disputes.
With the rise of smartphones, this solution has suffered setbacks. If Android phones do not root (increase permissions, so that mobile phone users or some software have higher permissions) will not be able to perform monitoring behaviors, especially when Apple mobile phones are in the case of screen recording and monitoring microphone, the upper left corner of the system will have high high corners of the system. Liang reminder. Therefore, such software has gradually been eliminated.

Another technical solution is traffic monitoring. Under normal circumstances, all Internet behaviors need to reach the public network through network equipment, and now the company will basically provide wireless networks for employees. All network traffic generated during this period will flow to the Internet through the network equipment, so only need to do traffic mirror images in the network export device, copy the data traffic flowing in the company to the analysis equipment, and can be used for internet behavior analysis. use.
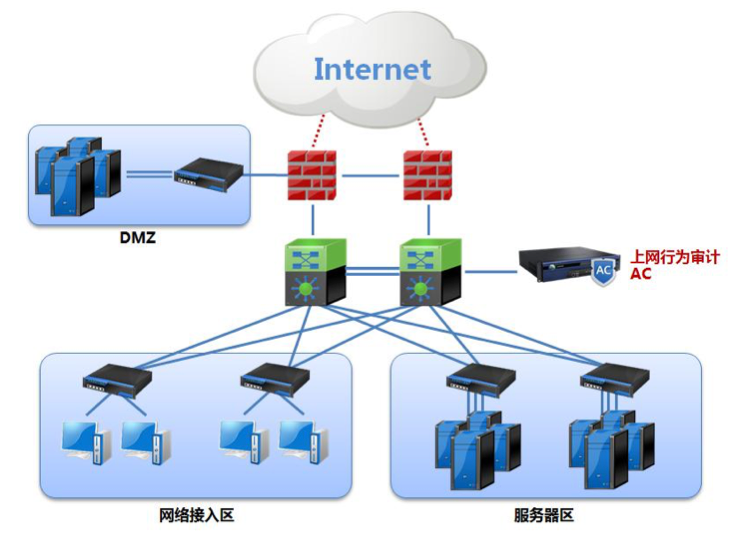
Behavior management product configuration
Photo source: Believe in the white paper management of AC Internet behavior management
According to the explanation, we generally call the company's internal network called the LAN, and the outside of the local area network is the Internet (public network). The device between the Internet and the local area network is called router (Router, and the wireless router in general families is actually a mixed product with router plus switch functions, which needs to be distinguished from the router used by enterprises).

You can understand the router as a finger passers -by. He maintains a routing table and tells how the traffic in the local area network should go and how the traffic entered the Internet reaches the device in the local area network.
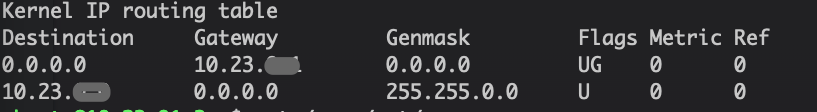
Route table, inform how the traffic goes
Photo source: Author screenshot
Of course, the devices in the local area network cannot be all received on the router. General Internet devices will connect to switches. The switch maintains a Mac table. There are specific MAC addresses (the hardware address of the network card) on the table. Essence

MAC table, recorded IP and actual devices of the physical address
Photo source: Author screenshot
High -level commercial products with network management functions can cooperate with the 802.1X protocol to verify the connected wired and wireless clients. The successful client that verifies the corresponding device will be directly associated at the management interface to associate with others in order to do behavior statistics.

If you are a Windows computer, you can try a small experiment. Press the Windows key + R key at the same time on the keyboard. The computer will pop up a input box and enter CMD in the input box. Then enter "IPCONFIG /ALL" in the black box that appears and press the Enter key. You will see the IP address of your current computer. One of the physical addresses is your MAC address.
In principle, your Mac is the only one in the world. You can also continue to use the command "ARP -A" to view the corresponding table of the IP address of the "neighbor" in your current local area network and the physical address.
How to judge the behavior of touching fish?
We return to this part of the fish -touch behavior management. In the introduction above, we already know how the company associates the equipment with you, so how do you judge that you are touching the fish?
As mentioned above, the product management product configuration chart, the company only needs to enter a copy of the traffic on the router or switch (generally the actual operation is to gather the switch, the small company's network equipment is simple here). This technology is called By -way mirror image.
If you compare the access and send and send it in and out, the bypass mirror is actually to copy your letter again, give it to the analysis device, and then slowly "see" the analysis equipment. At this step, your network behavior is naked in front of the boss.

Now let ’s take a look at how to“ see ”your traffic. After your traffic reaches the analysis equipment, the device begins to make behavior judgments or simple analysis according to different protocols. The traffic between the Internet is transmitted according to standard protocols, such as the common HTTP hyper -text transmission protocol (that is, an agreement to access the website). The picture below is the screenshot of the network traffic analysis tool Wireshark. We can see the author just open the official website of Shanghai Science and Technology Museum http://www.sstm.org.cn/.

Access traffic
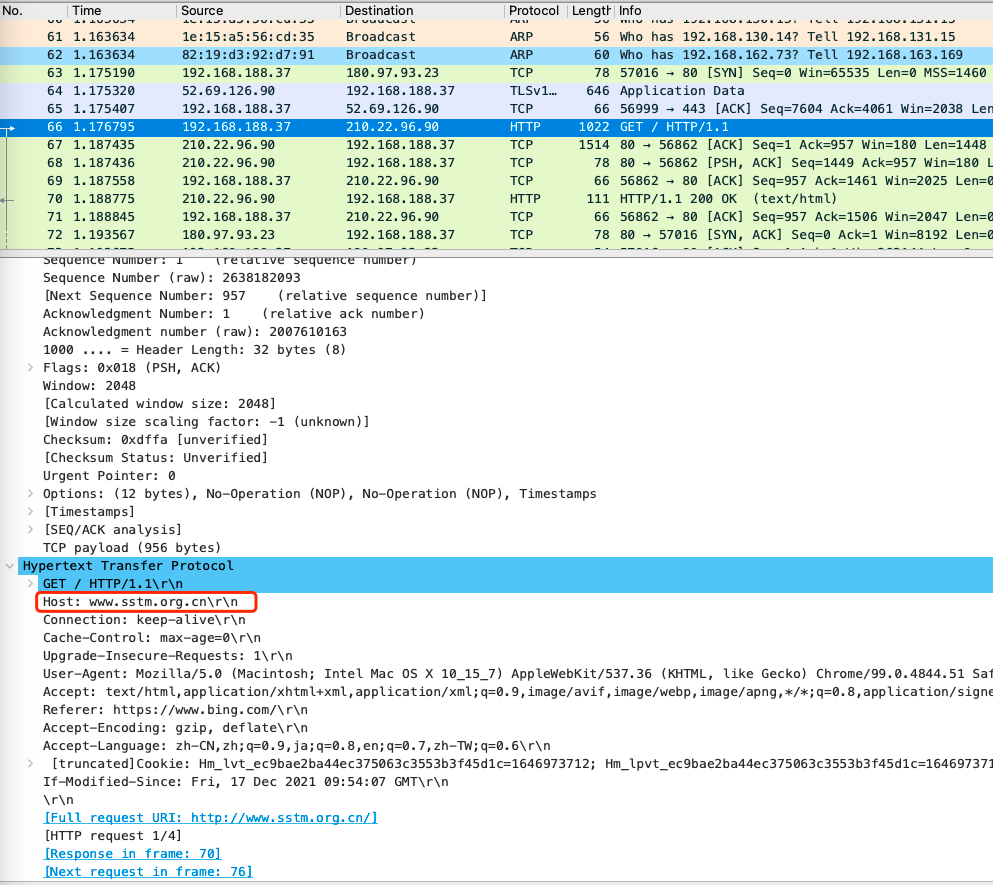
Photo source: Author screenshot
Because the Shanghai Science and Technology Museum does not use HTTPS, the recovery of the website will be displayed on the analysis device.
Response traffic
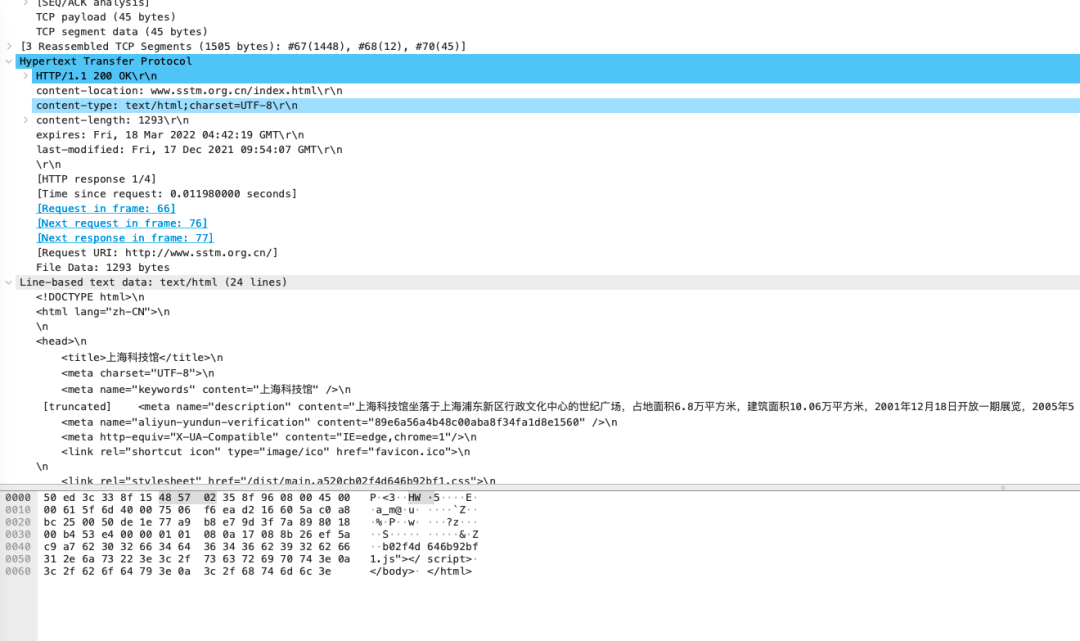
Photo source: Author screenshot
So the question is, will it be found if the user accesses the encryption website or the mobile APP traffic is used?
The answer is yes. Although the analysis device does not know the specific content you visit, you will know that you have had access and can count the traffic.
Here we need to know a protocol DNS. Our address on the Internet is the IP address of the public network. In order to access the convenience of the convenience and IP address, the providers of various websites and APP rarely provide IP directly to customers to access it, so it will provide an alias (ie, domain name) to customers.

The control relationship between domain name and IP
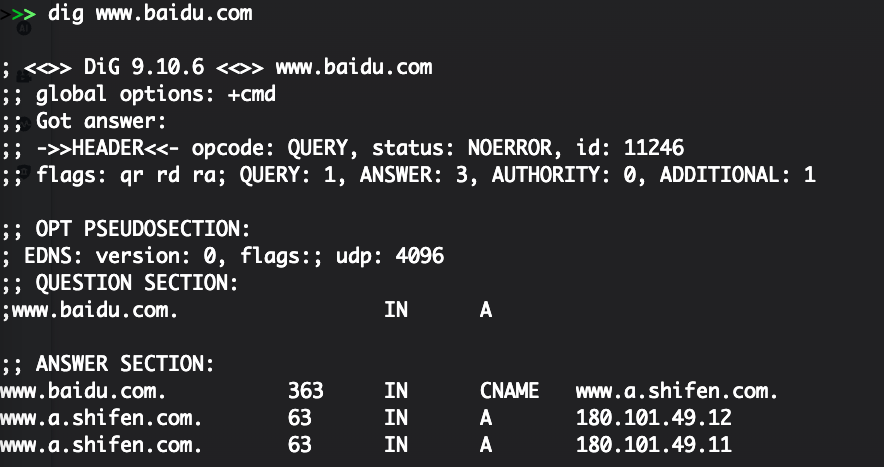
Photo source: Author screenshot
It can be seen from the figure that the actual analysis of www.baidu.com is on the two IPs of 180.101.49.12 and 180.101.49.11. Therefore, we actually visited http://180.101.49.12/ It was also Baidu.
When customer requests, the operating system will ask the DNS server's domain name IP address, and the request of this process will be recorded. The final IP is the address of the actual service.

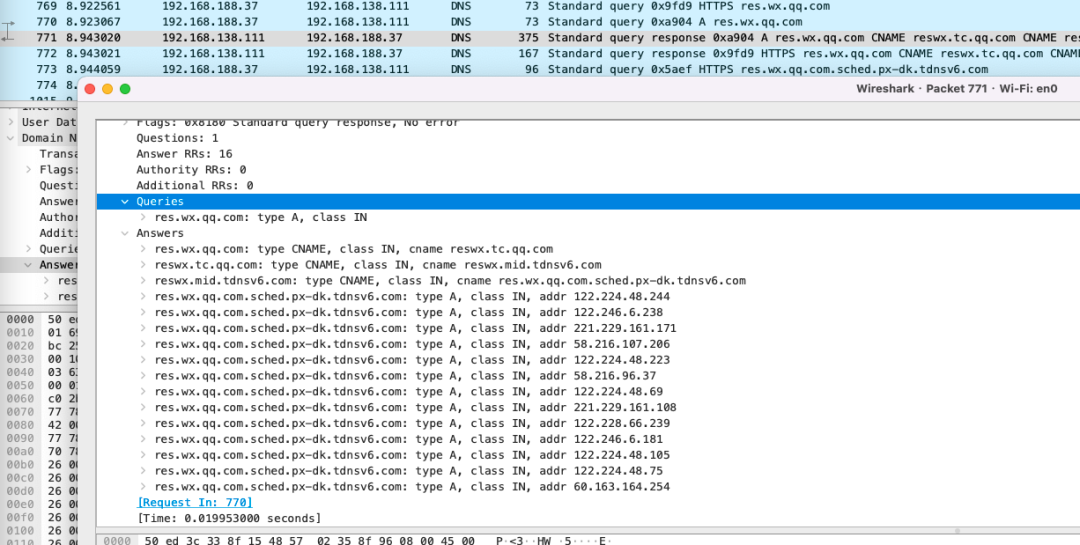
We see here that after opening WeChat, the IP of the inquiry of res.wx.qq.com is as follows, but the follow -up of the relevant traffic is considered to use WeChat traffic.
Photo source: Author screenshot
In addition, when the customer opens the vibrato, the monitoring will find the actual IP address from the following DNS query process (also found that live.douying.com Douyin live broadcast uses Alibaba Cloud's CDN acceleration).
Photo source: Author screenshot
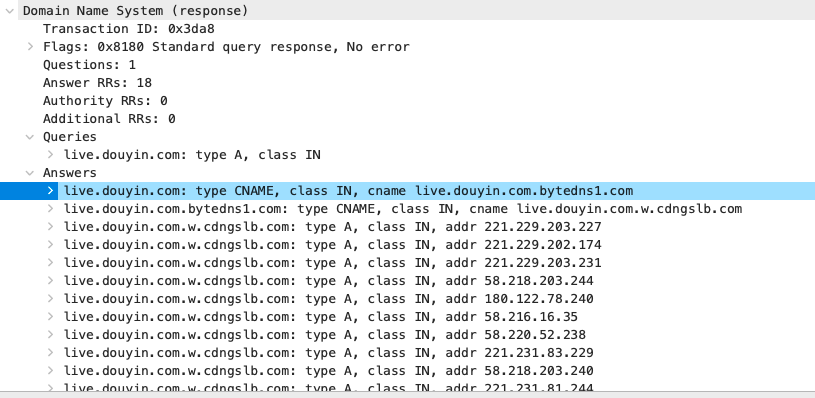
Of course, DNS is only one of the methods with domain name monitoring. Even if the HTTPS encryption flows, the analysis of the device cannot see the traffic content, but the request phase encryption protocol SNI head will still bring the domain name. Therefore, statistical follow -up communication traffic related to this IP can know your fish touching.
Photo source: Author screenshot
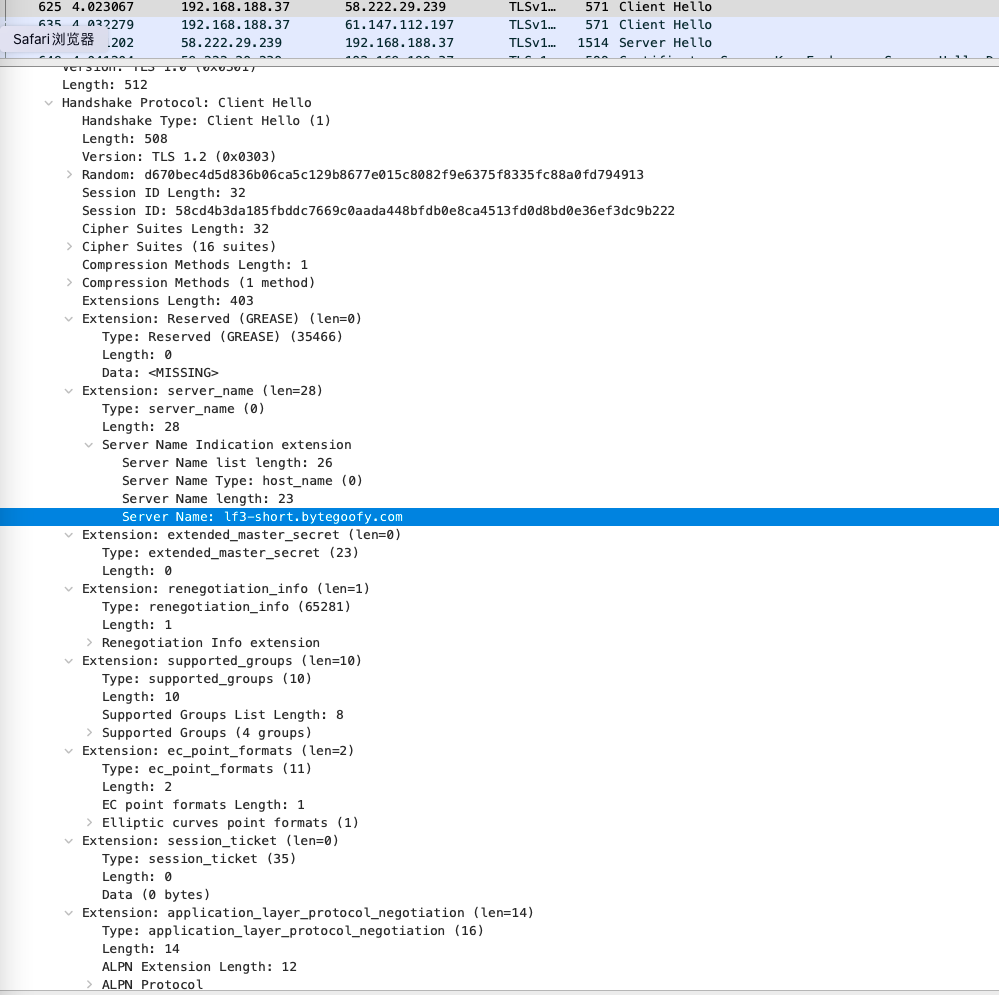
Therefore, in principle, your access marks on the Internet have nothing to do. Please do not treat the Internet as a place outside France.
Author: Qian Junyu, 7 years of cloud computing industry, focusing on safety and compliance related fields
Edit: One person white
—————
- END -
OEM decline, production reduction production announcement announced that low -priced failure color T

Popo || ContributionsIn the past few decades of development, perhaps we have exper...
Learn to implement Document No. 2 in Xin Guofa | Huang Mingjin: Do a good job of technical services

Document No. 2 of New Guofa clearly supports Guizhou to vigorously develop modern ...