Heavy disclosure: Hundreds of important information systems in China have been implanted by the United States in the U.S.
Author:Global Times Time:2022.06.29
On the 28th, the National Computer Virus Emergency Treatment Center and 360 Company released a special research report respectively. On the same day, another online attack weapon "Sour Fox" vulnerability attack weapon platform (hereinafter referred to as the "Sour Fox Platform" "). Relevant experts told the "Global Times" reporter that the "Sour Fox Platform" is the main battle equipment of the computer network invasion team of NSA under the NSA. The attack range covers the world. It is actively preparing for the launch of a larger scale.
Set up special servers for China and Russia, "Sour Fox Platform"
Recently, many Chinese scientific research institutions have discovered the traces of the "verification" Trojan horse program.
The research report released by the 360 Company on the 28th shows that according to the sophisticated US NSA confidential documentation: "Verification" is a small implantable Trojan, which can be deployed remotely or manually on any Windows system, from Windows 98 to Windows Server 2003 is adapted. At the same time, it has a 7 × 24 hours of online operation capabilities, allowing the US NSA system controller and data stealler to upload download files, remote running programs, obtain system information, forged IDs, and can be urgently destroyed in certain circumstances. With this weapon assistance, the US NSA can collect system environmental information on attack targets, and also provides conditions for installation (implanted) more complicated Trojans.
Earlier, 360 Company discovered and publicly disclosed that the US NSA used a series of network weapons to launch continuous attacks on government agencies, important organizations and information infrastructure targets including China, including China. Throughout the attack, the United States NSA will be implanted with the backdoor program represented by the "verification device", and lurks in the Internet terminals of the target users for a long time, and then initiates more complex network attack penetration through these backdoor programs.
The Trojan program is believed to be the standard program used by the NS "sour fox" vulnerability to attack the weapon platform. This situation shows that the Chinese scientific research units mentioned earlier have suffered a network attack on the US NSA "Sour Fox" vulnerability attack weapon platform.
According to the introduction, the "Sour Fox Platform" is an important position infrastructure of the NSA Specific Invasion Action Office (TAO) to carry out cyber spy operations on other countries. It has now become the main equipment of the computer network invasion team (CNE). The weapon platform is mainly used to break through the host system located in the internal network of the victim's target, and implant them into various Trojan horses and back doors to achieve persistent control. The sour fox platform adopts a distributed architecture and is composed of multiple servers. It is classified according to the type of task, including: garbage fishing mail, intermediate attacks, and postponation maintenance.
There are one or more "sour fox" project instructors under CNE. These instructors can lead one or more "sour fox" mobile groups. The action group includes multiple players to undertake directly supporting specific network invasion operations and maintaining acid. Responsibilities such as fox server. TAO deploys the sour fox platform server worldwide. The server is deployed in a distributed deployment according to the area where the target is located, including the Middle East, Asia, and Europe. Among them, the server with the number of nodes as XS is the main server of a number of tasks.
It is worth noting that the server number XS11 is clearly assigned to the British intelligence agency "British Government Communication Headquarters" (GCHQ) to carry out intermediate network attack operations. In addition, TAO has set up a dedicated "Sour Fox Platform" server for China and Russia's targets. The series of servers numbered FOX00-64 are used to support the loopholes of computer network invasion. For Chinese goals, the server of Fox00-6402 is specifically targeted at Russian goals.
Relevant experts from the National Computer Virus Emergency Treatment Center told the Global Times reporter that the "Sour Fox Platform" will detect the software and hardware environment of the target host before the use of loopholes. The "Sour Fox Platform" rule configuration file disclosed in the report shows that the weapon platform clearly means that computer anti -virus software in my country and Russia is the "technical confrontation" goal. Moreover, the United States has deployed online spy -spy server server on China and Russia on the International Internet for implantation of malicious programs and stealing information.
In order to maintain its network hegemony, the United States has "monitor all human beings", which has not changed in various US governments. On June 1 this year, the US National Security Agency Director and Commander of the Internet Command had confirmed that in the Russian conflict, the United States launched a series of offensive network operations against Russia to support Ukraine.
The expert also said that while the United States has intensified the global target to attack theft, the United States has spared no effort to "shout the thief to catch thieves", gather its so -called allies, and publicize the "Chinese Internet threat theory" "The truly mutually beneficial and win -win international economic and cultural exchange and cooperation plans, suppress China's corporate and news media that are legally operated abroad, and even incite the people's oppositional emotions, encourage the so -called folk" moral "hackers to launch a network attack to other countries.
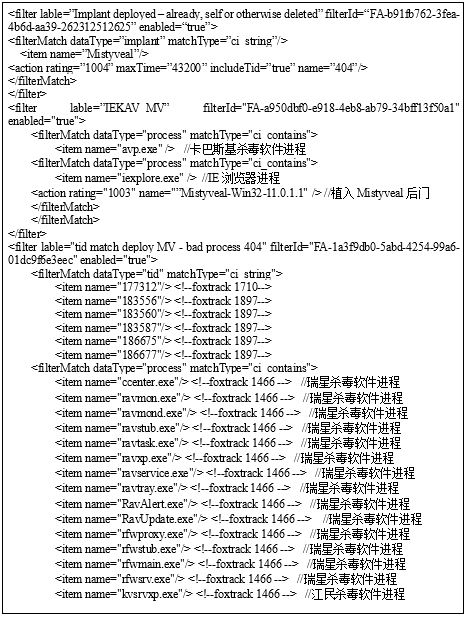
Filter rules on the "Sour Fox Platform" server, the filter focuses on the popular anti -virus software such as Kabasky anti -virus software, Rising anti -virus software, and Jiangmin anti -virus software in the target environment. The trace of the "verification device" Trojan horses in hundreds of important information systems in China
On the basis of the successful extraction of the "verification" Trojan program samples in the important information system of a domestic scientific research institution, 360 Company carried out scan detection in China as soon as possible. It was found that the different versions of the Trojan program were running in hundreds of important information systems in China. Important information systems implement network attacks. To this day, a number of "verification" Trojans procedures are still running in some information systems and transmitted intelligence to the NSA headquarters. The 360 company believes that "found the" verification device 'sample in the local network server or Internet terminal, indicating that these devices have suffered a network attack of NSA, the important information in the system has been stolen by NSA, and other nodes in the target system inner network are all all nodes in the inner network of the target system. May be infiltrated by NSA. "
In addition, according to the filter rules on the "Sour Fox Platform" server, it can be judged that the server mainly attacks China's host targets. The filter focuses on Kasperski anti -virus software, Rinxia anti -virus software, Jiangmin in the target environment Antivirus software such as anti -virus software such as anti -virus software was matched and judged by implanted conditions.
The 360 company believes that not only in China, other countries in important information infrastructure, but also running a large number of "verification" Trojan -horse procedures, and the number is far exceeding China.
The report released by the National Computer Virus Emergency treatment Center shows that even more terrible is that NSA uses these weapon platforms to cooperate with other "five -eye alliance" national intelligence agencies to establish a global network intelligence collection system, globally globally A large number of hidden intelligence collection servers and cover springboard servers have been set up, and a set of intelligence work mechanisms are established around the intelligence collection system. Normalization maintains the largest spy network in human history, and it continues to expand. Common threat.
Experts in the above also believe that despite the iron certificate, the United States will continue to carry out cyber spy activities and cyber warfare in the future. On June 22 this year, the US House of Representatives appropriation committee passed the US $ 761 billion national defense expenditure bill in FY2023, including the US Ministry of Defense's $ 11.2 billion network space activity budget, an increase of 8%over the previous fiscal year. Its cyber warfare troops increased from 137 to 142. The U.S. military is also comprehensively promoting JADC2's "land, sea, air, sky, and net" global command combat capabilities improvement plan. Its goal is to have an overwhelming military advantage in the global space.
The United States has recently introduced a series of bills to increase the scale of network security budget, strengthen its own key information infrastructure security level, and organize various domestic and international cyber warfare exercises. Safety research, restricting the output of sensitive network security technology. The approach to the United States can not help people doubt that they are actively preparing for a larger scale of online warfare.
FA server distribution and task use classification, of which the server of FOX00-6401 is specifically targeted at China, FOX00-6402 server is targeted at Russia

Global Times-Global Network Report Special Reporter Yuan Hong
- END -
China ’s US debt is against the US dollar, buying 292 European passenger planes, and US companies breaking defense, to promote communication between China and the United States

Recently, the largest news about China, the United States, and Europe is undoubted...
The CAC40 index of Paris France rose on the 7th

Xinhua News Agency: The CAC40 index of the Paris stock market in France closed at ...