Unified reply: Why don't the police help me chase the cheated money back?
Author:Sichuan Huayi Time:2022.08.05

A victim often asked: "I was deceived XX money, how could I chase it?" "Can the people who lie to me caught it?" Why can't the people hiding behind the back? "..." ...
Why can't the scammer catch it?
The scammers were caught. Why can't the money being chased back?
(Video transfer from: watermelon video. Author: egg brother bullish egg)
Fraud who disguise
1st floor, geographical disguise.
not
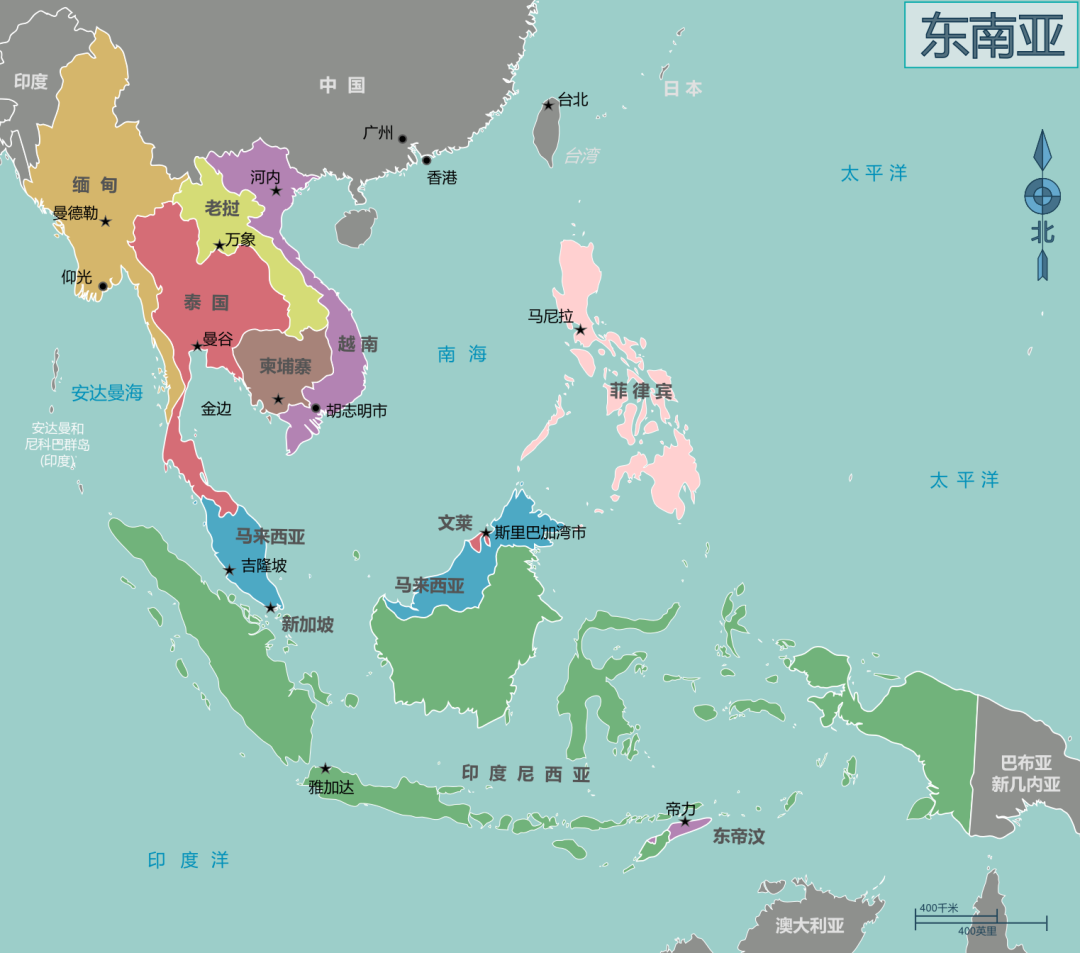
The scammers are proficient in anti -reconnaissance skills, make good use of various camouflage, and hidden everything that may expose their identity. The team is basically staying abroad. According to information tracked by many regions, most of the footholds of the fraud gangs are in Southeast Asia, and Southeast Asia has become the "fraud base" in Asia.
not
On the second floor, the identity camouflage.

not
A large number of lost and stolen second -generation resident identity cards were publicly sold in the online black market. Black market provides a steady stream of identity information resources for scammers. In the eyes of ordinary people, the real -name system is identification, but in the eyes of fraud, the real -name system has become one of the best means to avoid risks. Because the belonging to these identity information has nothing to do with the scammer.
not
The third layer, technical camouflage.

not
In fraud cases, the most difficult to break through is actually the technical camouflage. The most commonly used in SMS fraud is the pseudo -base station group. As long as one laptop, a software, a transmitter, you can send a good scam text message to the surrounding mobile phone users. Want to locate people with mobile phones? It's more difficult.
not
Floating IP and changing platforms are also two commonly used techniques for scammers. Floating IP is to use network springboard to continuously cover up the real IP and use false IP to implement network fraud. The change platform is to cover up its real number and change the phone to any you want. If you are lucky, you can query the true identity behind it. After the police prepare a series of documents such as air ticket passports, fly to the positioning location to check, and find that behind it is a private computer controlled by hackers, that is, "meat chicken". Professional money laundering fraud group
not

Professional money laundering groups mainly serve various types of fraud gangs. In the shortest time, they took out the money cheated by other scammers with "hard work" and returned them with legal channels. Type a series of numbers on the bank card into a real gold and silver that can be installed in your pocket. People at all levels of the group are dedicated, divided into labor, and responding at any time, forming an invisible but powerful spider web. As long as they have funds to touch the net, they will disappear without a trace under the action of this network.
not
The internal division of the fraud money laundering group is extremely fine, and is generally divided into five levels. The first layer is called "Shengyao", which is responsible for calling, sending information, mailing, etc.; the second floor is called "connecting county guys", responsible for connecting the "Shengyan" and the next level; the third layer is called " "Brush", as the name suggests, is responsible for brushing the POS machine and brushing the money to the online settlement center; the fourth floor is the "card guy", responsible for providing various bank cards to transfer it by itself; Responsible for getting money, you can get it yourself, or you can pay for others.
not
Strict discipline. The five levels of duties are clear and discipline is strict. There is no connection between the cross -level and no connection. Each level can only keep up with the upper layer, and you must not be able to connect with the upper level. In this way, even if the "withdrawal" is arrested, it is generally difficult to ask who the people at the higher level are and where they are, and they cannot catch the upper layer. The highest level of risk is very small.
not
Multi -road attack decentralized funds. For example, "Sound" deceives 200,000, it can be called "connecting county guys" A to deal with 100,000, "connecting county guys" B processing 100,000; "connecting guys" A can be called "brush guy" A to deal with 50,000, 50,000, and 50,000, 50,000, It is called "Brush Gelast" B to deal with 50,000; "Brush" A can also be called "Card" A to handle 10,000, "Card" B processing of 10,000; "A takes 10,000, and is called" withdrawal "b.
not
The intricate "children's account account"
not

The popular point of the "Children's Account" is that after receiving the fraud, the fraud will split the fraud funds, and use the bank account and the third -party payment platform to perform N+diversified transfers, and then use the "driver" to withdraw cash withdrawal. Essence Once the money enters this step, it is difficult to prove the source of funds and frozen accounts.
not
If the scammers want to be more safer, they will find a "water room". Many people may listen for the first time, such as its literal meaning, which is a new type of criminal den specifically used to wash white stolen money. Generally, "water rooms" serve multiple fraud gangs, fast whitewashing speed, and most of the final funds will flow to overseas accounts, which is difficult to recover.
not
Digital currency that is difficult to track
not

When scammers get fraud, the first thing that needs to be done is to safely wash the stolen money. By buying digital currencies such as Bitcoin, they can quickly and safely make money successfully transform, and perfectly avoid the law. Sanctions. not
not
Bitcoin uses a decentralized payment system, which has been separated from the traditional financial clearing system. It uses special means to jump between multiple wallet addresses with the same amount of scammers, thereby removing its original cryptocurrency information. Want to track the final address? Yes, go to the bottom of the dark online.
The bank card, telephone, and website information are fake. The degree of wisdom and courage to handle the case is far more than your imagination, so the best way to protect your "money bag" is not to wait for our police to solve the case, but to improve Awareness of anti -fraud.
The public security department has released the most complete 58 typical cyber fraud methods. These are cases of hard -earned money. Please ask everyone to check it quickly.
1. Improved identity fraud
1. Precurs leadership fraud: Criminal counterfeit leaders and other identities call to the heads of grassroots units. On the grounds of selling books, commemorative coins, etc., the deceived unit first pays the order payment, the handling fee, etc.
2. Precursing relatives and friends fraud: Use Trojan program to steal the other party's network communication tool password, intercept the other party's chat video materials, posing as the owner of the communication account to perform fraud The company's old chief fraud: Criminals have entered the company's internal communication groups, understand the information exchange between the boss and employees, and then pretend to send the transfer remittance instruction to the employee through a series of camouflage.
4. Subsidy funds, rescue funds, student aid fraud: posing as staff such as education, civil affairs, disabled federations and other staff, call and text messages to disabled, students, parents The bank card number instructed it to transfer the money on the withdrawal machine.
5. Performance of the public prosecutor's telephone fraud: Criminals are pretending to be a public prosecutor's staff call the victim, and requires the funds to transfer their funds to the national account for investigation on the grounds of being stolen, suspected of money laundering, and drug trafficking.
6. Forgery of identity fraud: Criminals disguised as "Gao Fushuai" or "Bai Fumei". After adding to friends to deceive feelings and trust, they immediately cheated money for various reasons such as tight funds and difficulties in their families.
7. Medical insurance and social security fraud: Criminals are pretending to be a medical insurance social security staff and lied that the victim's account was abnormal. Later, the staff of the judicial organs used a fair investigation and facilitated verification to seduce the victims to the so -called security account remittance.
8. "Guess who I am" fraud: Criminals call to the victim and let them "guess who I am", then take the identity of the familiar person and borrow money from the victim. Inside the bank card provided by criminals.
2. Shopping fraud
9. False purchasing fraud: Criminals are faked into formal micro -quotients, with discounts, discounts, overseas purchasing, etc. as bait. After buyers pay, they will be added to the reason that "the goods are deducted by the customs, and the tariffs are required to be paid" and so on. Payment items are implemented.
10. Return fraud: Criminals pretend to be a customer service such as Taobao and other companies, call or send text messages. They lied that the goods photographed by the victims were out of stock. They needed a refund to lure buyers to provide information such as bank card numbers and passwords to implement fraud.
11. Online shopping fraud: Criminals open a false shopping website or online store. After the host places an order, it is said that the system failure needs to be re -activated. Later, the false activation website was sent through QQ to allow the victims to fill in personal information and implement fraud.
12. Low -priced shopping fraud: Criminals release transfer information such as second -hand cars, second -hand computers, and customs from customs.
13. Lift installment payment fraud: The staff who pretended to be a shopping site who claimed that "because of the wrong bank system", the victims were deceived to go to the ATM machine to complete the installment payment procedures and implement the fund transfer.
14. Fragments: Criminals pretend to be a collection association, printed invitations to mail various places, saying that they will hold auction and leave a contact method. Once the victim contacted it, in the name of pre -paid evaluation fees, the victim was required to transfer the money to the designated account.
15. Express signing to accept fraud: The pretending to be a courier person calls the victim call, saying that it needs to sign the information but cannot see the information, and it needs to be provided by the victim. Then send the "goods" to the door. After the victim signed it, he called and said that he had signed a payment, otherwise the debt collection company would be in trouble.
Third, activity fraud
16. Publish false love transmission: Criminals published fictional tracing and helping posts on the Internet in the form of "love transmission", causing good online users to repost. In fact, the phone number left in the post is a fraud phone call.
17. Praise fraud: Criminals pretend to be a "praise with prizes" information, asking participants to send personal information such as names, telephones to social platforms. Implement fraud.
Fourth, fascinating fraud
18. Precursing well -known companies winning fraud: Pretending to be well -known companies, printed a large number of false pseudo -scratch cards in a large quantities, submitted and submitted various excuses such as personal income tax to seduce the victims to remit money to the designated bank account.
19. Fraud in the entertainment program: Criminals use the name of the hit section program group to send a short message to the victim's mobile phone group, saying that it has been selected as a lucky audience, and will receive huge prizes. Various excuses such as income tax are implemented.
20. Exchange points fraud: Criminal criminal calls, lied that the victim's mobile phone points could be exchanged, induced the victim to click on fishing links. If the victim enters the bank card number, password and other information according to the URL provided, the funds of the bank account will be transferred.
21. QR code fraud: Taking the price reduction and reward as the bait, the victim is required to scan the QR code to join the membership, but it is attached to the Trojan horse virus. Once scanned, Trojan will steal personal privacy information such as the victim's bank account and password.
22. Heavy money to ask for fraud: The criminals lied that they were willing to pay for the child, seduce the victims to be fooled, and then carried out fraud for various reasons such as paying sincere money and inspection fees.
23. High -paying recruitment fraud: Criminals use group information to recruit a certain type of professionals with a monthly salary of tens of thousands of yuan, asking the victim to interview at the designated place, and then perform fraud in the name of paying training fees, clothing fees, and margin.
24. Email scam: Criminals will send winning emails through the Internet. Once the victim contacts the criminals, the criminals will request the victims to remit money for various reasons such as paying personal income tax and notarization fee to achieve the purpose of fraud. Five, fictional dangerous fraud
25. Fictional car accident fraud: Criminals are required to transfer the other party immediately on the grounds that the victim's relatives or friends encounter a car accident and need an emergency handling of traffic accidents.
26. Fictional abduction fraud: The criminal fictional and relatives of the criminals are abducted. If you want to rescue the hostages, you need to pay the payment immediately to the designated account and you will not report to the police, otherwise the ticket will be torn.
27. Fictional surgery fraud: Criminals are required to be treated on the grounds that the victim's children or parents need emergency surgery and require the victim to be treated.
28. Fictional dilemma for fraud: Criminals have released false situations such as serious illness and difficulties in social media, and they have won sympathy for the majority of netizens to accept donations.
29. Fictional parcels of Tibetan drug fraud: Criminals are required to transfer money to the national security account for a fair investigation on the grounds that the criminals were found to be found in the victim's wrapping.
30. Occupible pictures of obscene pictures: Criminals collect photos of public officials, use computers to synthesize obscene pictures, and attach to the receipt account to mail the victims for threat to threaten and extort money.
31. Fictional abortion surgery: Criminals pretend to be a son to send text messages to their parents, and make full use of the characteristics of the elderly's distressed son to seduce the victims to transfer.
6. Consumption fraud in daily life
32. Fa filling the landlord SMS fraud: The criminals pretended to be a SMS message, saying that the landlord's bank card had been changed and asked to put the rent into other designated accounts.
33. Telephone arrears: Criminals are pretending to be a staff member of the communications operating enterprise to call the victim or directly play the computer voice. On the grounds of their phone arrears, the debt funds are required to transfer the debt funds to the designated account.
34. Television arrears: Criminals allocated calls from the staff, saying that cable television arrears in the name of the victims in the name of the victim will allow the victim to make up to the designated account.
35. Shopping tax refund fraud: After obtaining information such as the purchase of real estate, cars, etc., the criminals have obtained information, and the tax refund can be handled on the grounds of tax policy adjustment to seduce the victim on the ATM machine to perform transfer operations.
36. Funding fraud: Criminals pretend to be airline customer service. On the grounds of "flight cancellation, providing refund, and signing service", the ticket purchasers have been deceived to conduct remittance operations and implement serial fraud.
37. Booking fraud: Criminals make false online booking companies web pages to publish false information to seduce the victims at a lower fare. Subsequently, the victim was required to remit money again for reasons such as "unsuccessful booking tickets" to implement fraud.
38. ATM machines to show fraud: Criminals block the ATM machine outlets in advance, and paste the false service hotline to seduce users to contact them after the card "swallow", set the password, and take the user to take out the bank card after the user leaves. , Steal the user card in cash.
39. Swipe card consumption fraud: Criminals are posing as a bank card consumption to leak personal information on the grounds of bank card consumption, posing as the UnionPay center or public security police to set up bank accounts and passwords to implement crimes.
40. Lure remittance fraud: The criminals directly request the deposit of a bank account in the direction of a bank in a group message. Since the victim is preparing to remit the money, after receiving the information of such remittances Put into the scammer account.
7. Fishing and Trojan virus fraud
41. Pseudo -base station fraud: Criminals use pseudo -based stations to send online banking upgrades to the masses, and 10086 mobile malls to exchange cash for false links. Once the victim clicks, it implants a Trojan horse with bank accounts, passwords and mobile phone numbers on its mobile phone. In this way, crimes are implemented.
42. Fishing website fraud: Criminals are upgraded on the grounds that the bank's online banking upgrade is required to log in to the fishing website of counterfeit banks, and then obtain information such as bank accounts, online banking passwords, and mobile phone transaction codes to implement fraud.
8. Other new types of illegal fraud
43. School News SMS link fraud: Criminals send fraud SMS with links in the name of "School News!! Essence
44. Traffic processing illegal SMS fraud: Criminals use pseudo -base stations to send counterfeit violations to remind the SMS. Such SMS includes a Trojan horse link. After the victims are clicked, they send text messages to cause the calls for calls. Account information, then stole the bank card.
45. Wedding electronic invitation fraud: Criminals can induce users to click to download through electronic invitations, and they can steal information such as bank accounts, passwords, and correspondences in the mobile phone, and then steal the user's bank card, or give the user's address book to the address book of the user Friends sending borrowing fraud text messages.
46. Mobile app fraud. Publicize the mobile phone app through online social software, and there are "customer service" and "experts" for guiding operations after downloading and registering.
47. Financial trading fraud: Criminals spread the inside information and trends of false stocks through the name of the Internet, telephone SMS, etc. in the name of securities companies. Check the home of the victim.
48. Credit card fraud: In the media, the media published a high overdraft credit card advertisement. After the partner contacted it, he required continuous transfer of the party to pay the handling fee and intermediary fee. 49. Loan fraud: Criminals send information through group information, saying that they can provide loans for those with shortage of funds. The monthly interest is low and no guarantee is required. Once the owner believes it is true, the other party will implement fraud in the name of prepaid interest, security deposit.
50. Copy mobile phone card fraud: criminals send information, say that mobile phone cards can be replicated, and mobile phone call information can be monitored. Many people actively contact the suspect due to personal needs, and then deceived money by the other party in the name of copying cards and prepayments.
51. Fictional porn service fraud: Criminals leave a phone call to provide porn services on the Internet. After the victim is contacted, they say that they need to pay before they can come to provide services.
52. Provide test fraud: Criminals call for candidates who are about to take the exam, saying that they can provide test questions or answers. Many candidates are anxious to achieve success, transferred the down payment of the benefits to the designated account in advance, and later found that they were deceived.
53. Still the account number and brush reputation fraud: After the criminals steal the social platform account of the merchant, they release the push news of "recruiting part -time network part -time jobs to help Taobao sellers brush their reputation and earn commission". The victim was reputable according to the other party's request, and later found that he was deceived.
54. Precursing triad extortion fraud: Criminals first obtain information from the victim, occupation, mobile phone number and other information, calling for self -proclaimed triad personnel, and the employment of people must be harmed.
55. WIFI WIFI: Free fishing WiFi in public places. After the owner connects these free networks, the transmission of traffic data is transmitted to steal the photos, phone numbers, and various passwords in the mobile phone, and extract the machine owner to extract the owner of the owner blackmail.
56. Pick up a bank card with a password: Criminals deliberately discard the bank card with a password, and indicate the "phone number of account opening banks". Card and deposit money on the scammer's account.
57. The account has abnormal changes in funds: stealing the victim's online banking account and password, and the illusion of capital flowing on the bank card. Then counterfeit customer service requires the victim to provide the verification code received by their mobile phones to further fraud.
58. If the number is changed, please pay: After the criminal obtains the address book information of the owner through illegal channels, the counterfeiter sent a text message to the contact person in the mobile phone, claiming to change the new number, and then conduct the contact person in his mobile phone. Fraud.
Finally reminded: Once deceived, as long as you wake up the time "fast", the police "fast", and the police officer stop paying "fast", the funds will be paid in the bank card or account. Stop payment.
not
Publicity tens of millions of times, never read it carefully.
After deception, the case was urgently reported, and the case was urged every day.

The scammers are overseas, and the police are also embarrassed.

Conditions for cases and prevention are the key.
The source is blocked, where will it be cheated.
For more information, everyone should promote it.
Source | Panda anti -fraud
Edit | Miao Guihua Responsible | Ren Dan
Editor -in -chief on Duty | Supervision of Lei Changsheng | Yang Tianhai


- END -
[Centennial Action] The "Hundred Days of Action" of Ganzhou Police attacked!These are the key points ...

In order to implement the summer public security crackdown rectificationHundred Da...
Carry out the training of administrative work in accordance with the law to promote the renovation and improvement of the ancient city

Recently, Nixang Street, Zhenping County, Henan Province organized administrative ...