Xintong Academy Excellence Partner Conference -XDR Lands on Practical Technical Analysis
Author:Chinese science and technology Time:2022.07.21
On July 19, under the guidance of the Ministry of Industry and Information Technology Administration, China Information and Communication Research Institute (hereinafter referred to as "China CITIC Institute") held a demonstration center of the Excellence Verification (hereinafter referred to as the "Excellent Center") in 2022 Partner conference.

The release of the results of the excellence center and partners of this conference, Wei Liang, honorary director of the Excellence Demonstration Center/Deputy Dean of the China Information and Communication Research Institute, director of Excellence Demonstration Center/Director of the Security Institute of China Information and Communication Research Institute Meng Nan, the deputy director of the Security Institute of the China Information and Communication Research Institute of the Demonstration Center, attended the meeting and delivered a speech. He is convinced that Gu Liming, an expert in service safety technology, was invited to participate in the conference and published the theme sharing of "XDR's key technical analysis".

Since 2021, my country has formulated a number of policies and regulations to regulate the construction of corporate network security, including the "Regulations on the Security Protection of Key Information Infrastructure" and "Regulations on the Management of Network Product Security Vulnerability". Provide norms and guidance for national and enterprise information security construction. At the same time, driven by the increasingly deepening of digital transformation, a large number of key business assets of users are distributed in more and more networks. Advanced, lurking, industrialized new types of attacks have grown barbaric growth, and traditional and decentralized safety equipment is difficult to fight. The user purchased a bunch of safety equipment, but could not work together, and the security incidents were still frequent.
Gu Liming pointed out that this is bound to put forward new requirements for the safety construction of security manufacturers and users. It is necessary to learn new security concepts and upgrade new security technologies to solve the problem of threat detection response -XDR is born.
Based on the technical research and accumulation in the field of threatening detection response, it is convinced that the service has formed a complete interpretation of key technologies and core values of XDR:
Fully understanding XDR key technology, building strength barriers
1. Comprehensive remote test data collection
XDR aggregates and analyzes the remote test data collected by the network cloud, which can deeply understand whether the security risks and attacks in the objects protected or monitored. Essence Comprehensive telemetry data collection is a huge progress in security big data analysis. By saving bandwidth and data costs, it lays the foundation for large -scale and SaaS -based deployment.
2.AI -driven automation threat hunting
XDR needs to find a variety of attacks with high bypasses and evasion skills. It is necessary to find very targeted orientation attacks, which means that XDR must provide behavior detection capabilities based on attack skills -threatening hunting. At the same time, considering the scarcity of hunting experts, XDR cannot rely on human -oriented hunting, and needs to be based on AI or machine learning to form a joint force by multi -dimensional detection to deal with attack threats in various complex scenarios.
3. Automation response
For attacks that have penetrated into internal, XDR needs to prevent attack behavior as soon as possible, at the same time identify key risks, eliminate harm eradication, and reinforce the weak points to be used. The entire process pays great attention to timeliness and needs to be completed before the attacker. Therefore, the mechanism that relies on automation can effectively reduce MTTR (Mean Time to Response, average response time).
I am convinced that the service has launched a number of cooperation with the excellent center in terms of innovative technological research, security capacity standards and verification. In the future, I hope to play the advantages of both parties in terms of standardization, standardization, and intelligence of security innovation products to jointly promote the development of the network security industry.
- END -
Note that there are also "assassins" in the air ticket!Some flight attendants are more expensive than tickets
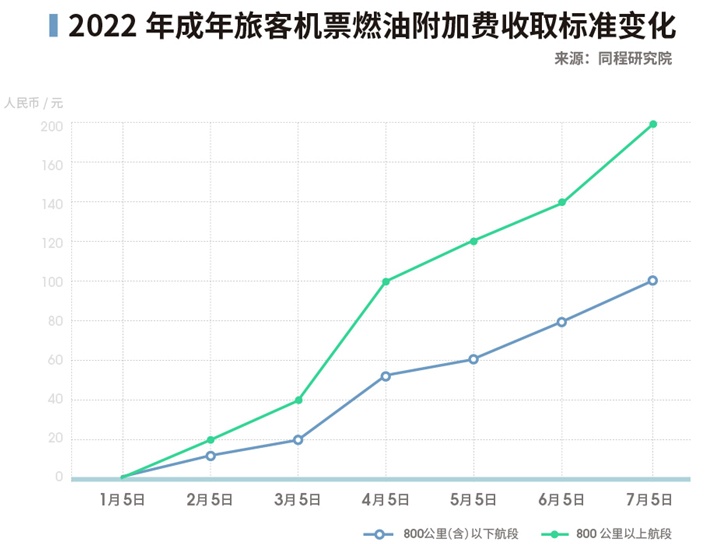
Why is the fuel cost of machine construction to 250 yuan? Buy more than 500 air ti...
The city's first textile non -heritage innovation conversion base settled in Fengtai

On June 24th, the Symposium on the Development of Textiles and Non -Heritage and t...