Apple hot search first!Related to hackers!Involved in iPhone, IMAC, etc.
Author:China Economic Network Time:2022.08.21
On August 20, Apple once again appeared on the Weibo hot search list again. This time, it is related to hackers! Earlier, in 2020, a senior information security researcher from Google said that there was a major loophole in the equipment such as Apple mobile phones, and you could get all your information without contacting your mobile phone.
iPhone, IMAC and other products have serious security vulnerabilities
According to the Associated Press on the 20th, Apple, the United States, released two security reports on Wednesday local time. Two reports disclosed that the company's smartphone iPhone, tablet computer iPad, and IMAC computers had serious security vulnerabilities.
These vulnerabilities may allow potential attackers to invade user equipment, obtain management authority, and even fully control the equipment and run the application software.
Apple calls on users to download the latest updates, repair loopholes
In the security update released on Wednesday, Apple said that the vulnerability may have been used for attack behavior.
What kind of loopholes are it?
"This is what we call zero vulnerabilities, that is, the loopholes that have been used by hackers before the company discovered and could respond." Jamie Collier introduced.
According to reports, the device affected by this vulnerability covers almost all apple products. Among them, mobile phones include iPhone 6s and later models; tablets include the fifth -generation and subsequent iPad, all iPad Pro, and iPad Air 2; the computer is Mac running MacOS MONTEREY. In addition, the vulnerability can affect some models of the iPod.
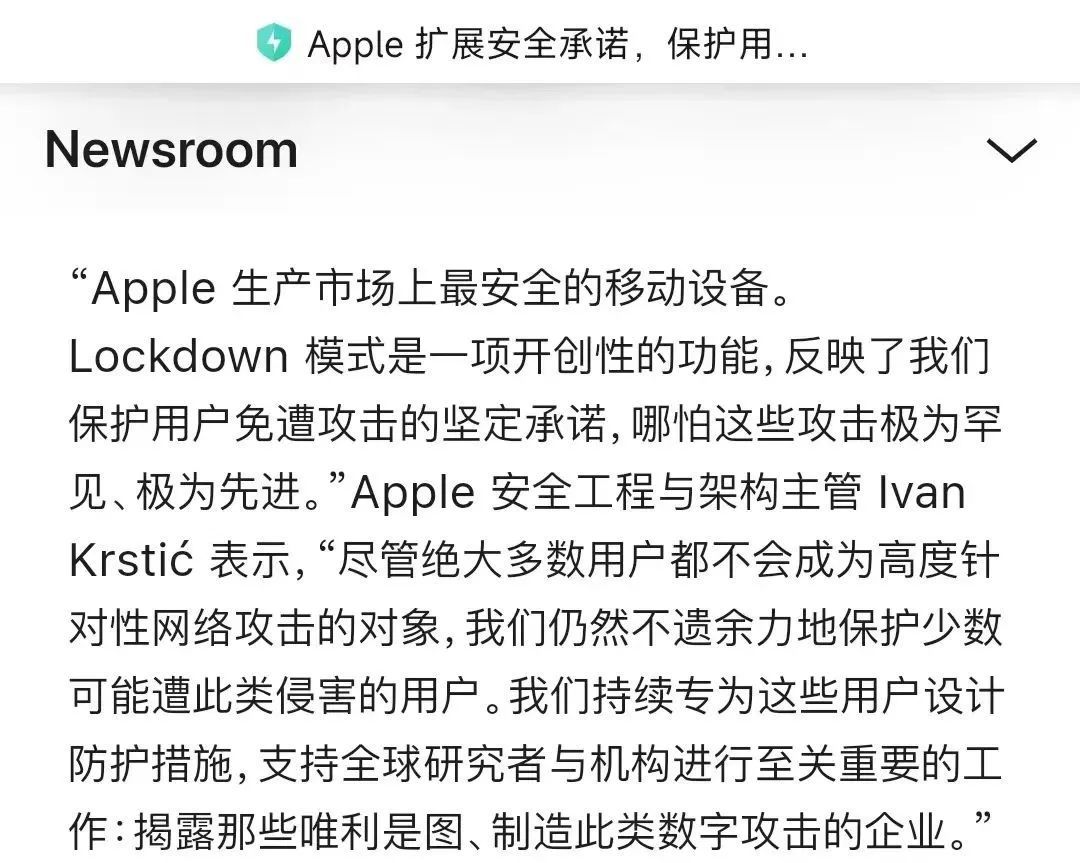
On August 19th local time, Apple called on users to download the latest updates immediately to repair loopholes. Currently on Apple's official website, Apple still declares "the safest mobile devices in the production market."
In 2020, Google researchers have exposed iPhone privacy vulnerabilities
On December 5, 2020, the website of "Russia Today" and a number of foreign science and technology websites reported that a senior information security researcher from Google discovered that there were major loopholes in Apple mobile phones and other devices. All your information.
According to this researcher, the key to this vulnerability is that Apple's network protocol referred to as AWDL. At present, Apple mobile phones, tablets, watches and other devices are using this network protocol. For example, Apple users can easily transmit photos and files to other Apple devices through AirDrop, which is based on this AWDL protocol.
With this vulnerability, Google's researchers spent 6 months and successfully controlled an Apple phone in the next room. The invasion process can access all the data on the mobile phone, including browsing information, downloading photos, and even opening the camera and microphone for monitoring and monitoring.
Researchers say that invasion hackers not only do not need to touch the device, but may never have seen the equipment he invaded. What's even more terrible is that even if the user shuts down the AWDL protocol, the hacker still has a way to reopen it. Not only Apple phones, other devices of Apple can also be "controlled" through this method.
Researchers said that although he spent half a year alone to invade. But users cannot take it lightly. This process is much easier for a hacker team. Apple has fixed this vulnerability in the new system in May 2020. However, Google researchers said that even if Apple did not tell users the loopholes, the entire process was completely unaware of the user.
- END -
Linyi, a grass -roots community party secretary, won the title of "Qilu Most Beautiful Retired Military" in 2022
On the evening of August 1st, the results of the 2022 Qilu Most Beautiful Retired Military selection co -sponsored by the Propaganda Department of the Shandong Provincial Party Committee, the Shando
The roads of waterlogging and collapse in Fujian are interrupted, and more than 150,000 people are transferred to the people

The heavy rain continued, causing disasters such as waterlogging, landslide, and r...