Be careful of "drinking tea"!Details of American Internet Attack West Engineering University exposure
Author:Look at the think tank Time:2022.09.13
According to the Global Times, the reporter learned from the relevant departments on the 13th:
In Northwestern University of Technology, the National Security Agency (NSA) network attack incident, the sniffing secret network weapon named "tea drinking" is one of the most direct "culprits" that lead to a large amount of sensitive data.
In this regard, network security experts suggested that in the process of informatization, it is recommended to choose domestic products and "zero trust" security solutions.

National Security Agency (NSA) headquarters
This article is integrated from the WeChat public account "Southern Daily" (ID: NF_DAILY) from the Global Times, CCTV News, Xia Ke Island, and People's Daily. The original first published on September 13, 2022. The original title was "Be careful of" drinking tea "! Western University of Technology was found by the "culprit" attacked by the American Internet ", which does not mean watching think tank views.
1
Publicity of the technical details of the beauty of the United States
On September 5, relevant Chinese departments announced to the outside world that Northwest University of Technology had previously stated that it was attacked by overseas network attacks. The attacker was the National Security Agency (NSA) specific invasion action office (TAO).
What institution is the "Specific Invasion Action Office" (TAO)?
It is understood that the "Specific Invasion Action Office" was established in 1998. It is currently a tactical implementation unit that specializes in the US government specializing in the implementation of large -scale network attacks on other countries. The National Security Agency set up 10 units in the centers in the United States and Europe.

The person in charge of the attack theft of Northwestern Polytechnical University was Robert Joyce. This person was born on September 13, 1967 and entered the National Security Agency in 1989. He has served as deputy director and director of the "Specific Invasion Action Office", and is currently the head of NSA network security of the National Security Agency.
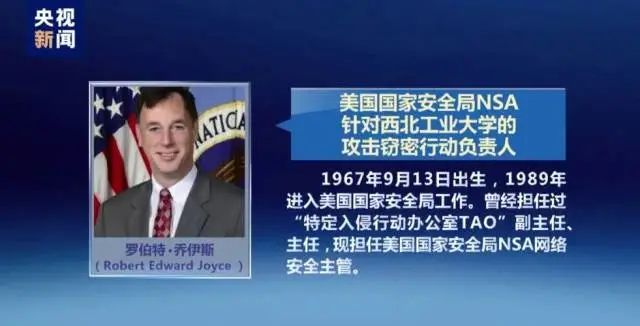
In this invasion, the National Computer Virus Emergency treatment Center and Beijing Qi'an Panku Laboratory further analyzed. In the latest survey report, the technical details of the United States' attack on attacks were made public:
TAO uses "tea drinking" as a tool for sniffing theft, implanted it into the internal network server of Northwestern University of Technology, stealing the login password of remote management and remote file transmission services such as SSH, so as to obtain access permissions of other servers in the internal network and realize The inner network moves horizontally and sends other high -value servers to other sniffing secrets, persistent control and concealed disappearance network weapons, causing large -scale, persistent sensitive data theft.
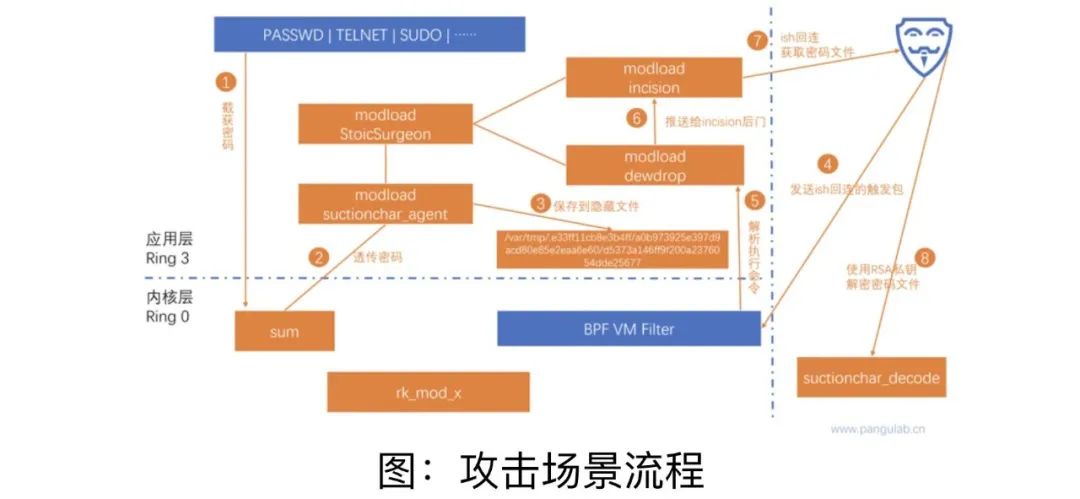
According to technical analysis and research, "tea drinking" can not only steal the account password of a variety of remote management and remote file transmission services on the server, but also have strong hiddenness and environmental adaptability.
Network security experts said that after the "tea drinking" is implanted into the target server and network devices, it will disguise itself into a normal background service process, and use a modular method to send malicious loads in stages. It has a strong concealment. It is difficult to find. "Tea Drinking" can be operated hidden on the server, monitor the user's input on the terminal program of the operating system console in real time, and intercepts various user names and passwords, like the "voyer" standing behind the user.
Cyber security experts introduced: "Once these username passwords are obtained by TAO, they can be used to attack the next stage. Even if these usernames password access to other servers and network devices, they will steal files on the server or send other delivery of other. Network weapon. "
According to the previous survey report, through the analysis of evidence, the technical team has accumulated a total of more than 1,100 attack links that attackers in the Northwest Institute of Technology's internal infiltration, more than 90 instruction sequences of operations, and positioning from the invaded network devices that have been invaded. A number of stolen network device configuration files, sniffing network communication data and passwords, other types of logs and key files, and other main details related to attack activities.
In addition, technical analysis shows that "tea drinking" can effectively integrate and link with other NSA network weapons to achieve "seamless docking". In TAO's incident of cyber attacks on Northwestern Polytechnical University, the "Tea Drinking" sniffing theft tools and BVP47 Trojan Programs were cooperated with other components to implement joint attacks.
2
Attacking West Engineering University is just the tip of the iceberg
The report also pointed out that with the gradual deepening of the survey, the technical team also found the "tea drinking" attack traces in other institutions outside Northwestern Polytechnical University. Network attack activities.
It is worth noting that in the multiple cyber attack activities implemented by the United States, the US IT industry giants have repeatedly appeared.
For example, in the "Prism" plan, the US love department has the authority of senior administrators and can enter the servers of Microsoft, Yahoo, Google, Apple and other companies at any time, and the long -term secrets are tailored. In the hacking tools used by the "Formula" organization announced by the "Shadow Broker", Microsoft, Cisco, and even some Chinese Internet service providers' "zero vulnerabilities" (0Day) or back doors appeared.
In February of this year, Beijing Qi'an Pan Ancient Laboratory disclosed that the "Formula" of the hacker organization belonging to the NSA uses top backdoors to launch a "electric curtain action" network attack for more than ten years to 45 countries and regions in China and Russia. The attack target includes well -known universities, scientific research institutions, communications industries, government departments, etc.; 360 companies' surveys in 2008 also showed that China is one of the long -term key network attack targets in NSA. These network attacks can not only steal other countries' intelligence, but also destroy key infrastructure such as power, water conservancy, telecommunications, transportation, and energy, and even cause catastrophic consequences to public data, public communication networks, public transportation networks, and public services.

U.S. monitoring the world is already a public secret. Taking the well -known "prism" project as an example, 122 foreign leaders were listened to the United States in 2009 alone; as of 2011, more than 100 million credit card information from Europe, Africa and the Middle East were "tracked" in the United States. After a meal, the US intelligence department collects nearly 5 billion mobile phone call records and 2 billion mobile phone short information around the world.
In February 2020, a number of US media issued a joint investigation report, saying that since the 1970s, the United States has cooperated with the former West German intelligence department to secretly control Swiss encrypted equipment suppliers and steal intelligence in more than 120 countries and regions around the world. , Carry out no different monitoring. "American network hegemony is revealed."
Avoid similar incidents at Northwestern Polytechnical University, network security experts suggest:
1. Users to strengthen key servers, especially network operation and maintenance servers
2. Regularly change the administrator of the server and network equipment
3. Strengthen the audit of internal network traffic
4. Discover the abnormal remote access request in time
At the same time, in the process of informatization, it is recommended to use domestic products and "zero trust" security solutions. ("Zero trust" is a new generation of network security protection concepts. No one, equipment, and systems inside and outside the network default.)
Network activities can easily cross the border
Internet attack has become
Pioneer of contemporary continuous struggle
Network security is part of national security
It is necessary to establish a Chinese, independent and independent
Network protection and confrontation capabilities
As ordinary citizens remember the following points






Uncle Kuju
"Adventure of Life"

CITIC Publishing Group
Heat waves, cold waves ... extreme climate events are becoming more frequent,
The risk of extinction of species is close to it.
Don't fall into despair first, this book will let you see,
How to find a way out.
Scholar Sol Hansen,
Live the surprise adventure of natural creatures with text.

- END -
[Revolutionary soldiers in the most beautiful new era] He Xianda: "Fight for the first, be a trump card"
[Revolutionary soldiers in the most beautiful new era]Speaking of He Xianda, the leader of a missile brigade of the Rocket Army, the officers and soldiers gave up their thumbs up, and even claimed tha
Zelei supports "Taiwan against the mainland"?Is it a conspiracy, or did he open the river?

Military and Military Secondary Point Author: Da YiwanAt noon on June 13th, Beijin...