Northwestern Polytechnical University was disclosed by NSA network attack details
Author:Jiangsu News Time:2022.09.05

Today (5th), the National Computer Virus Emergency Treatment Center and 360 Company released a survey report on Northwestern Polytechnical University suffering from overseas network attacks. The report shows that the source of the Internet attack is the National Security Agency (NSA).
NSA uses 41 network attack weapons to steal data
Northwestern Polytechnical University, which has been attacked, is located in Xi'an, Shaanxi. It is currently a key university engaged in aviation, aerospace, navigation engineering education and scientific research. It has a large number of national top scientific research teams and high -end talents and undertakes multiple national key scientific research projects. Police said that because Northwestern Polytechnical University has a special status and sensitive scientific research, it has become a targeted goal of this online attack.
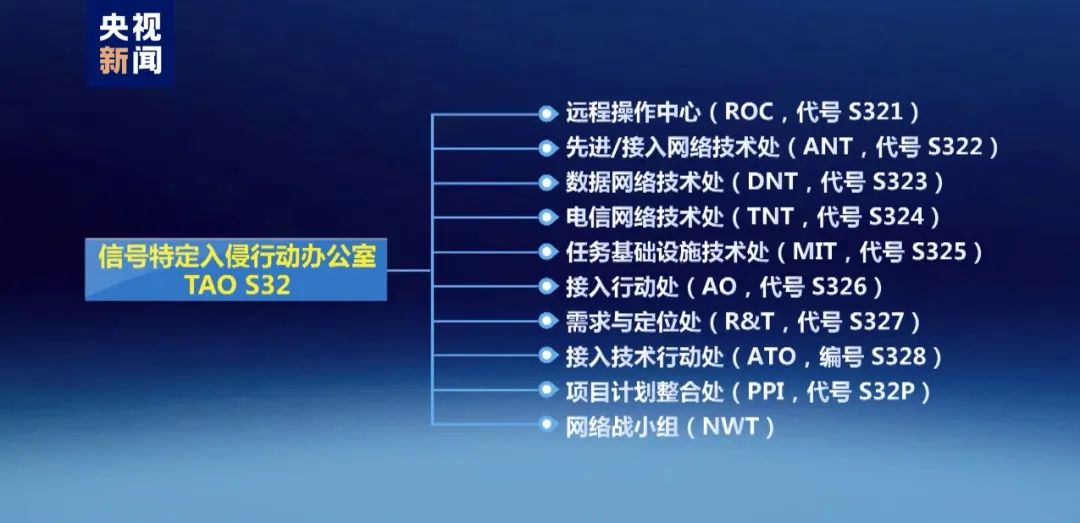
The survey report shows that the National Security Agency continues to attack the stealing of Northwestern Polytechnical University and steal core technical data such as the school's key network equipment configuration, network management data, and operation and maintenance data. There have been 41 special network attack weapons and equipment, and only 14 different versions of the back door tool "cunning different criminals" (NSA naming).
Through the analysis of evidence, the technical team has accumulated a total of more than 1,100 attack links that attackers penetrated within Northwestern University of Technology, more than 90 instruction sequences of operation, and positioned multiple stolen networks from the invaded network devices. Equipment configuration files, sniffing network communication data and passwords, other types of logs and key files, and other main details related to attack activities.

The technical team divides the weapon category used in this attack event into four categories, including:
Vulnerability attack breakthrough weapon
Persistent control weapons
Sniffing theft weapon
Concealment
The survey report disclosed that the National Security Agency used a large number of network attacks to attack weapons to conduct secret hacking activities for leading enterprises, governments, universities, medical care, scientific research and other institutions in various industries in my country.
The survey also found that the US National Security Agency also used its controlling network attack weapon platform, "zero -day loopholes" and network devices to conduct non -difference voice monitoring of mobile phone users in China for a long time, illegally stealing SMS content of mobile phone users And wireless positioning. Cover up the real IP
Carefully disguise the network attack traces
The survey report disclosed that in order to hide its network attacks on Chinese information networks such as Northwestern Polytechnical University, the National Security Agency made long -term preparations and carefully camouflage.
The analysis of the technical team found that the Specific Action Office (TAO) under the National Security Agency (TAO) will carry out long -term preparations before the start of the operation, mainly anonymous attack infrastructure construction. The "Specific Invasion Action Office" uses the two "zero -day loopholes" use tools for the SUNOS operating system to select tools to select more network applications such as educational institutions and commercial companies in China as the attack target; the attack is successful; Later, the NOPEN Trojan program was installed to control a large number of springboard.
The "Specific Invasion Action Office" has used 54 springboard machines and proxy servers in network attacks against Northwestern Polytechnical University, mainly distributed in 17 countries including Japan, South Korea, Sweden, Poland, and Ukraine, of which 70%are located in the surrounding China Countries, such as Japan and South Korea. Among them, a springboard used to cover up the real IP is carefully selected, and all IP belongs to the non -"five -eye alliance" country.

The technical team also found that before the start of the relevant network attack activities, the National Security Agency cooperated with many large -scale Internet companies in the United States to provide the management authority of a large number of Chinese communications network devices that can be grasped to the US National Security Agency and other intelligence agencies. The important information network that continues to invade China's domestic information is very convenient.
"Specific Invasion Action Office"
What institution is it?
So, what is the institution of the "Specific Invasion Action Office"?
It is understood that the "Specific Invasion Action Office" was established in 1998. It is currently a tactical implementation unit that specializes in the US government specializing in the implementation of large -scale network attacks on other countries. The National Security Agency set up 10 units in the centers in the United States and Europe.
The person in charge of the attack theft of Northwestern Polytechnical University was Robert Joyce. This person was born on September 13, 1967 and entered the National Security Agency in 1989. He has served as deputy director and director of the "Specific Invasion Action Office", and is currently the head of NSA network security of the National Security Agency.
Network security experts said that it is understood that the invasion office office represents the highest level of global cyber attacks. The large number of attack weapons they master are equivalent to the universal key in the Internet, which can be arbitrarily entered and out of the target equipment it wants, so as to thus Stealing intelligence or destruction.

The survey report believes that Northwestern Polytechnical University has publicly released a statement that has been attacked by overseas network attacks, and actively adopting defense measures to learn from victims of online attack activities of the National Security Agency around the world. The follow -up network attack behavior is strongly drawn from.
Source/ CCTV News
Edit/Tao Tao

© Jiangsu News
focus on
- END -
Yunnan Entering the era of medical insurance expenses online payment era
The dual channel management mechanism allows ordinary people to buy negotiating me...
Come to Guangzhou Tianhe Yiyuan to see the Guangdong Fine Art Teacher Works Exhibition

Text/Yangcheng Evening News All -Media Journalist Ji Min Correspondent Hu Shuotang...