Be careful of "drinking tea"!The technical details of the US Attack West Engineering University are open
Author:Beijing News Time:2022.09.13
The technical team also discovered the "tea drinking" attack traces in other institutions outside Northwestern Polytechnical University. It is likely that Tao used "tea drinking" to launch large -scale network attack activities on China.
The full text is 2070 words, it takes about 4 minutes to read
According to CCTV News, today, the National Computer Virus Emergency Center released the "Analysis Report of the NSA Network weapon" Tea Drinking ", which unveiled the technical details of the National Security Agency (NSA) network attack Northwestern Polytechnical University. Northwestern University of Technology had previously stated that it was attacked by an overseas network, and the attacker was the Specific Action Office of the National Security Agency (TAO).
Bleak
"Tea drinking" is one of the most direct "culprits" that lead to a large amount of sensitive data.

According to technical analysis, of the 41 network weapons attacking Northwestern Polytechnical University, the sniffing secret network weapon named "Tea Drinking" is one of the most direct "culprits" that cause a large amount of sensitive data. The network weapon is mainly aimed at the Unix/Linux platform, and its main function is to steal the remote access password on the target host.
The NSA's Specific Invasion Action Office (TAO) uses "tea drinking" as a tool for sniffing, implanted it into the internal network server of Northwestern Polytechnical University, stealing remote management and remote file transmission services of SSH, Telnet, FTP, SCP and other remote file transmission services Passwords to obtain access permissions of other servers in the internal network, realize the horizontal movement of the intranet, and send other high -value server to other high -value servers to other olfactory secrets, persistent controls, and hidden disappearance network weapons, causing large -scale and continuous continuity Sex sensitive data theft.
Bleak
Other institutions except Western Gong University also have traces of being attacked by the Internet
With the gradual deepening of the survey, the technical team also discovered the "tea drinking" attack traces in other institutions outside Northwestern Polytechnical University. It is likely that TAO uses "tea drinking" to launch large -scale network attack activities to China. Essence
The details of the "Tea Drinking Tea" of the American NSA Web Weapon "are as follows:
I. Overview
During the survey of the National Computer Virus Emergency treatment Center, the Northwest Polytechnical University was investigated by an overseas network attack. For "SuctionChar") (see the "Northwest Polytechnical University" released on September 5, 2022, "Report on the Investigation of Northwest University of Technology (one)"). The National Computer Virus Emergency Treatment Center and Qi Anxin Company conducted a technical analysis of the network weapon. The analysis results show that the network weapon is a "sniffing stealing weapon", which is mainly aimed at the Unix/Linux platform. The remote access account password is stealing.
2. Technical analysis
After technical analysis and research, this network weapon is aimed at the Unix/Linux platform and cooperates with other network weapons. The attacker can control the malware to perform specific secret stealing tasks by pushing the configuration file. Various user names and passwords, including SSH, Telnet, FTP, and other remote service login passwords, can also steal the user name password information stored in other locations according to the configuration.
This network weapon contains a number of components such as "Authenticate", "Decrypt", "Decode Module", "Configuration Module", "Agent" "," De decode module "," Decode Module "," Configuration Module "," Agent " The results of the technical analysis are as follows:
(1) Verification module
The main function of the verification module is to verify the identity of the call (parent process) before the "tea drinking" is called, and then decrypt and decodes to load other malware modules. As shown in Figure 1.

(2) Decrying module
The decryption module is a general module, which can be decrypted by other module calls to the specified file. The RSA+RC6 encryption algorithm similar to the NOPEN remote control Trojan (see the "NOPEN remote control Trojan analysis report") is used. as shown in picture 2.

(3) Decoding module
Similar to the decryption module, the decoding module is also a general module. It can be called by other modules to decoding the specified file, but the self -coding algorithm is used. As shown in Figure 3.
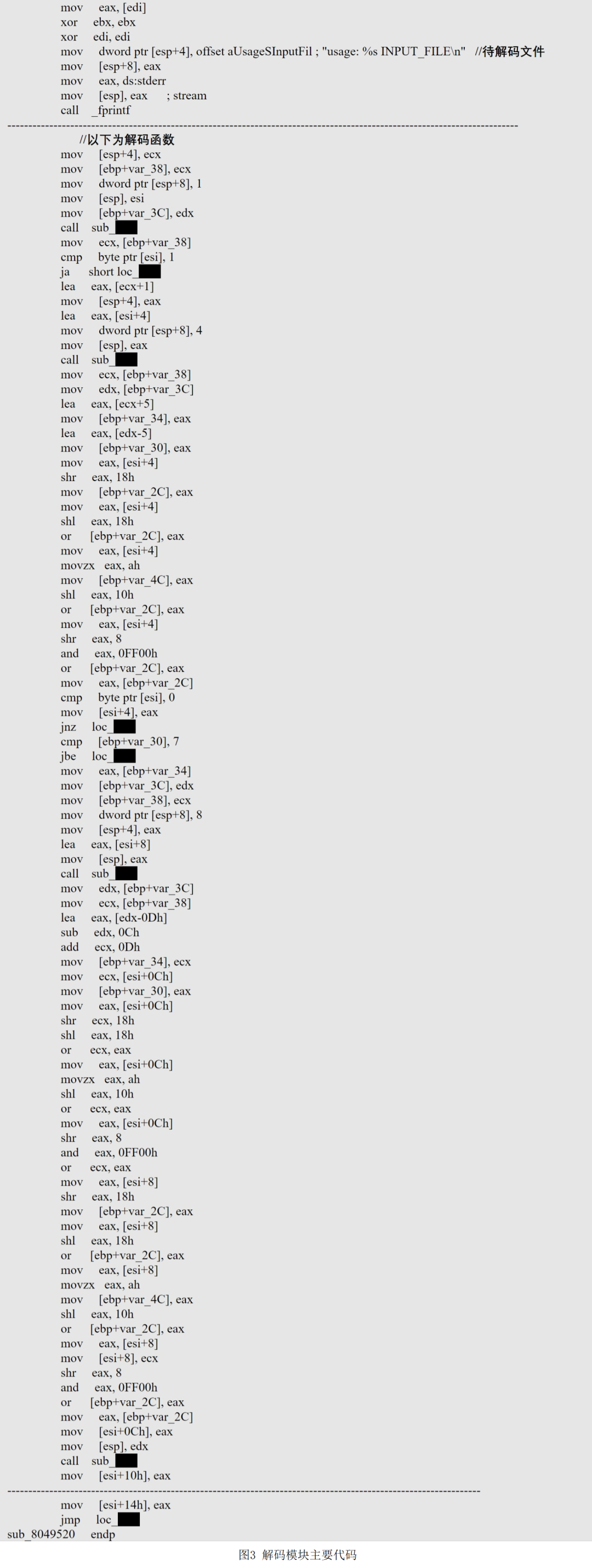
(4) Configuration module
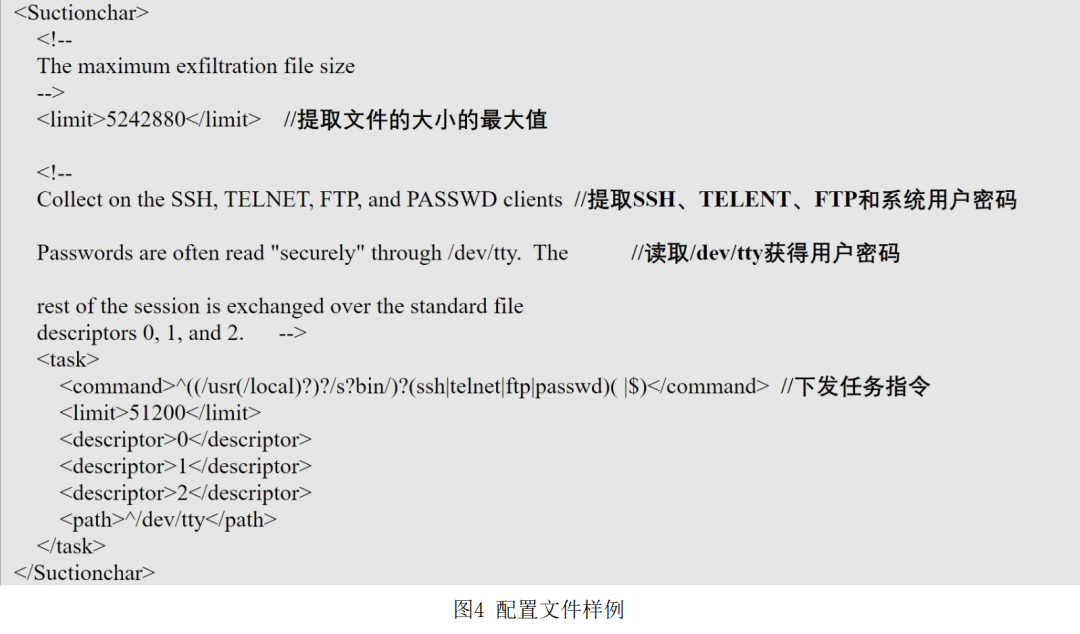
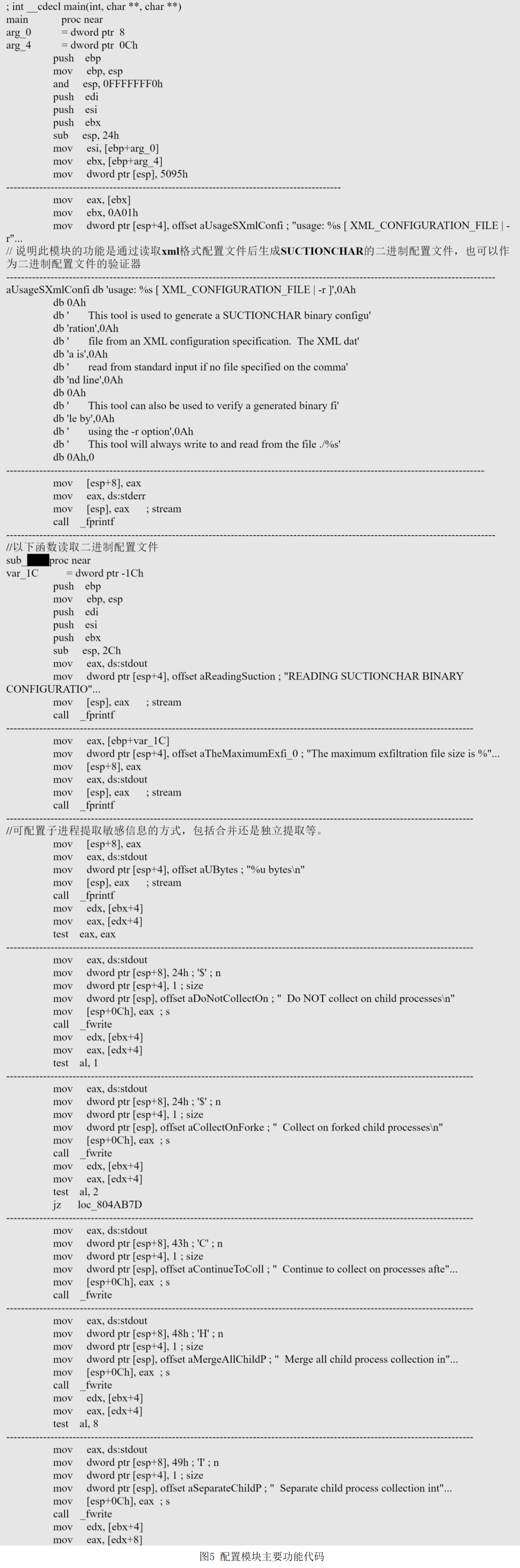
The main function of the configuration module is to read the instructions and matching rules in the XML format configuration file sent by the attacker remotely, and generate binary configuration files, so as to call the "monitoring module" and "spy module" after the victim host is found on the victim console. content. As shown in Figure 4 and Figure 5.
(5) Spy module
The main function of the spy module is to extract the corresponding sensitive information from the victim's host and output to the specified position according to the instructions and rules issued by the attacker.

(6) Other modules
During the analysis, we also found two other modules, which are configuration file generating modules and guardian modules. Among them, the function of the configuration file generating module may be to generate an INI temporary configuration file, and the guardian module and the spy module have high code similarity, which may be a variant produced for different versions of systems.
3. Summary
Based on the results of the above analysis, the technical analysis team believes that "tea drinking" is complicated, highly modular, supports multi -threaded, and has a wide range of adaptation of the operating system environment, including freeBSD, Sun Solaris system, and Debian, RedHat, CentOS, Ubuntu and other Linux. The distribution version reflects the advanced software engineering capabilities of developers. "Drinking Tea" also has good openness, which can be effectively integrated and linked with other network weapons. It uses encryption and verification to enhance its own safety and concealment. Extract information such as login username passwords. In theory, you can also extract all the information you want to get. It is a powerful network weapon tool with advanced functions and strong concealment. In this attack on Northwestern Polytechnical University, the U.S. NSA's Specific Invasion Action Office (TAO) uses "tea drinking" as a sniffing secret tool to implant it into the internal network server of Northwestern Polytechnical University, stealing SSH, Telnet, FTP, FTP , SCP and other remote management and login passwords for remote file transmission services, so as to obtain access permissions from other servers in the internal network, realize the horizontal movement of the internal network, and send other high -value servers to other sniffing secrets, persistent control categories and durable control categories The concealed disappearance network weapon has caused large -scale and persistent sensitive data theft. With the gradual deepening of the survey, the technical team also discovered the "tea drinking" attack traces in other institutions outside Northwestern Polytechnical University. It is likely that TAO uses "tea drinking" to launch large -scale network attack activities to China. Essence
Source CCTV News, News Network
Editor on duty Kang Hee
- END -
The latest notice of the Hebei Provincial Medical Insurance Bureau is suspended!

July 15thThe latest notice of the website of Hebei Medical Insurance Bureau issued...
List of members of the Twelfth Committee of the Communist Party of China and the alternate members, the list of members of the 12th Disciplinary Inspection Commission of the Communist Party of China

The Twelfth Congress of the Chinese Communist Party of China successfully complete...