"Early" and "post -afterwards" of network security: Who needs to be responsible for the use of UFIDA software?
Southern Finance All Media Reporter Wu Liyang Intern Wu Feng Beijing reportedRecently, many social media and security technology communities have claimed to have encountered the .Locked suffix to ex
Hurry up and update!Apple exposes security vulnerabilities

Recently, the fruit has been brushed to the iPhone 14 series from time to time.How...
Apple hot search first!Related to hackers!Involved in iPhone, IMAC, etc.
On August 20, Apple once again appeared on the Weibo hot search list again. This t...
I am convinced that the actual combat of XDR is the golden eyes, how can I make it?
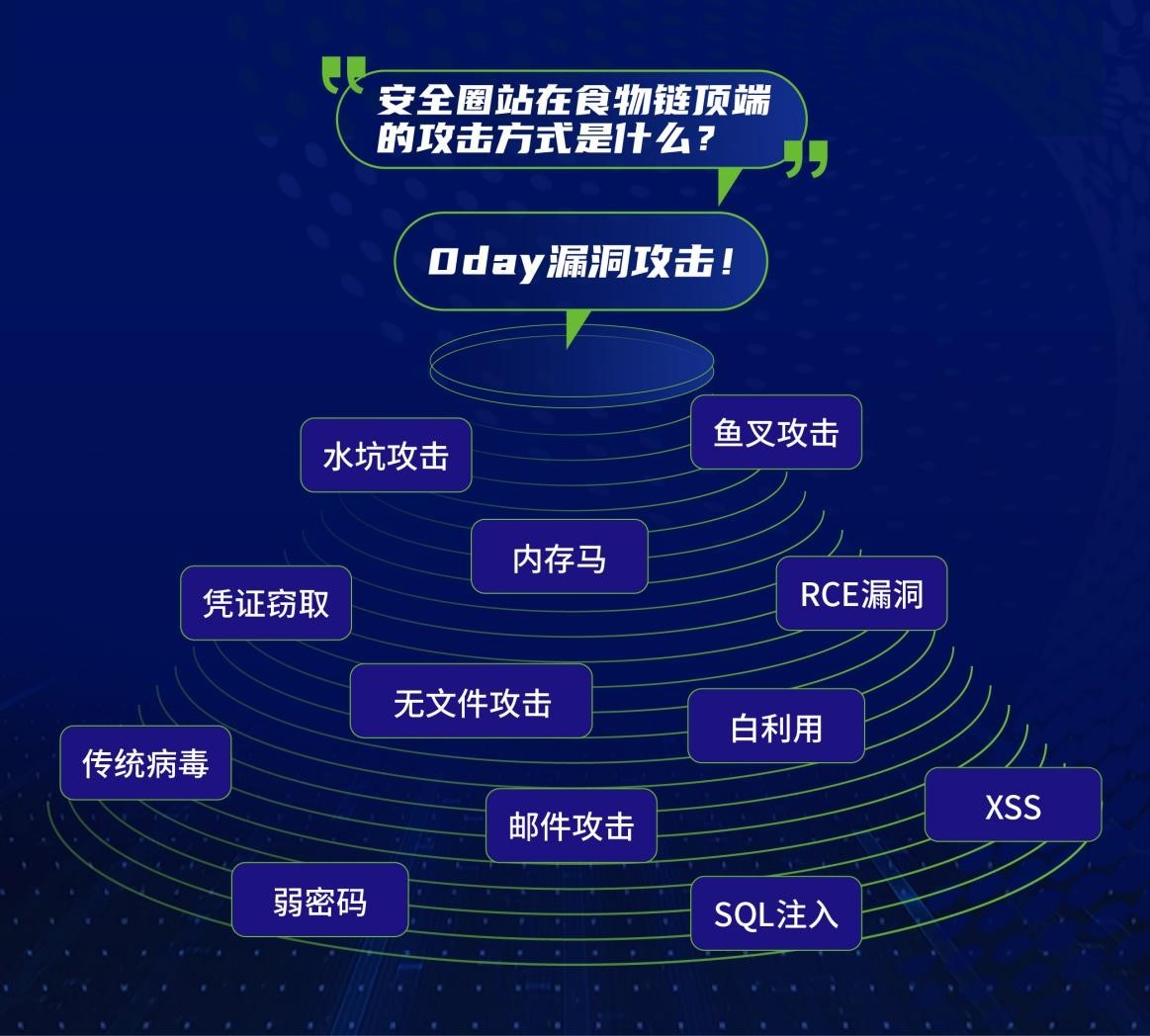
On the morning of June 13, 2022, he was convinced that the XDR security expert Xia...
Extremely review | Men take their girlfriends to eat seafood only to pay plastic bags, don't let the self -checkout of the "back door" to theft

Ji Mu News commentator Qu JingRecently, a man in Jiangsu took his girlfriend to He...
You believe what he said ...

He says:This investment website is really making money. You have to believe me, I ...